Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
The developer of a SWAT-based first-person shooter video game has allegedly lost four terabytes of data, including source code, to a ransomware attack.
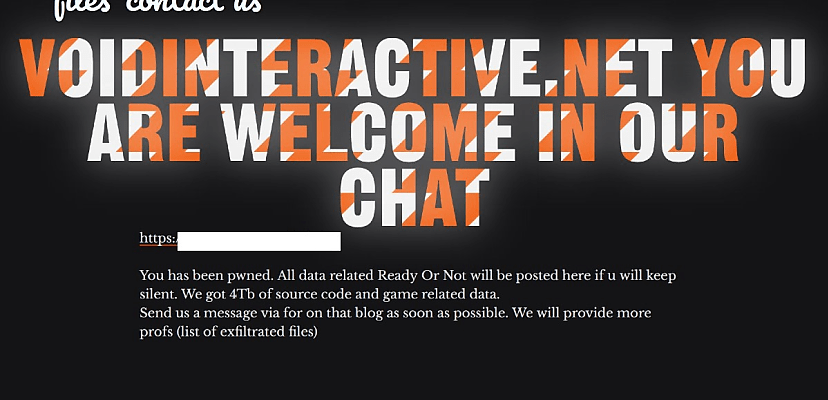
The D#NUT ransomware gang claims to have successfully exfiltrated four terabytes of data from Void Interactive, the developer of the popular tactical shooter video game Ready or Not.
“Voidinteractive.net you are welcome in our chat,” D#NUT declared on its dark net leak site on 14 March.
“You has been pwned. All data related Ready Or Not will be posted here if u will keep silent. We got 4Tb of source code and game related data.”
The gang do not appear to be native English speakers.
“Send us a message via for on that blog as soon as possible. We will provide more profs (list of exfiltrated files),” it said.
To add proof to its claim, the gang shared a link to the Imgur image-hosting site and a screenshot of a list of various builds of the game in what appears to be a dev environment. More than 20 distinct builds are listed for both PC and consoles, as well as various performance test builds.
The screenshot appears to be authentic.
D#NUT – whose leak site features a lurid illustration of the gang’s namesake – is a relatively small ransomware operation. Since it was first observed by threat tracker FalconFeeds.io in April 2023, the gang has claimed 10 victims, with Void Interactive being the latest. Half of its victims have been North American organisations, with the rest spread across Europe and the UK.
However, the authenticity of the gang’s claims has been questioned by some observers. On 5 February, the gang claimed to have successfully hacked the US Department of Defense, stealing documents related to a host of contractors, but one security analyst poured cold water on the claim.
“I would approach this claimed ‘breach’ by donut ransomware with caution and scepticism,” the X account CyberKnow posted on the same day.
“All the claimed US defence contractor victims have been posted to leak sites in the past year or two.”
There are some earlier incidents that D#NUT has taken responsibility for, while in March 2023, the Monti ransomware group claimed it had, in turn, hacked D#NUT. The hack was a revenge attack, with Monti claiming that D#NUT “stole 100,000 usd didn’t fulfill the terms of the deal”.
There are even earlier reports of the gang’s activity. BleepingComputer first observed D#NUT – though it was simply Donut back then – in August 2022, when it attacked a Greek natural gas company. In November of the same year, however, BleepingComputer characterised D#NUT as an affiliate for other ransomware operations, including Hive and Ragnar Locker, though it did note that D#NUT was beginning to deploy its own encryptor.
Cyber Daily has reached out to Void Interactive for comment.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.