Share this article on:
Powered by MOMENTUMMEDIA
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
This is the second installment in a four-part blog series offering an in-depth breakdown of the four essential pillars of industrial cybersecurity: Reveal, Protect, Detect, and Connect. The objective of this series is to help security leaders understand the unique challenges of meeting these needs in an industrial context, as well as the time and resources Claroty has invested into cohesively addressing these challenges in an unparalleled manner.

In the first installment in this series, we took an in-depth look at why visibility into industrial environments is often challenging yet very necessary, as well as what capabilities are necessary to overcome those challenges. After revealing your industrial environment in its entirety, the next step is to protect against risks inherent to that environment.
Broadly speaking, protecting against industrial cybersecurity risk is a three-step process:
Gaining visibility into complex industrial environments is challenging enough, but even so, this visibility can do little to inform your cyber-defense strategy unless you also have the technology in place to identify risk and assess its implications in the context of your unique environment.
As a very straightforward example, security teams should understand that allowing remote access to their organization’s industrial environment without robust, OT-specific protections in place introduces enormous risk they cannot afford to leave unmitigated. Unfortunately, it’s not always so simple.
ICS vulnerabilities have rightfully garnered growing interest from cybersecurity researchers and practitioners in recent years, but since any given industrial environment has more vulnerabilities than could ever be mitigated, managing the risk posed by security flaws requires a more nuanced assessment. The first requirement for making such an assessment is the ability to match your granular asset inventory against a comprehensive database of which security flaws are present in which specific asset models.
In qualitative risk analysis, risk = likelihood x potential impact. To understand the risk posed by a given vulnerability, you must be able to assess its feasibility of exploitation by adversaries, as well as the extent to which exploitation would grant the ability to access critical systems, further infiltrate your network, or otherwise disrupt operations.
Claroty Continuous Threat Detection (CTD) empowers users to understand risk on an asset-by-asset basis with Asset Risk Scoring, which quantifies the likelihood on the basis of a vulnerable asset’s accessibility to threat actors due to its network location, communications with other assets, and number of open ports. Meanwhile, potential impact is gauged based on the nature of vulnerabilities present, asset criticality, and the extent to which an asset is able to spread malicious content to other assets based on its policies, baseline behaviors, privileges, and protocols.
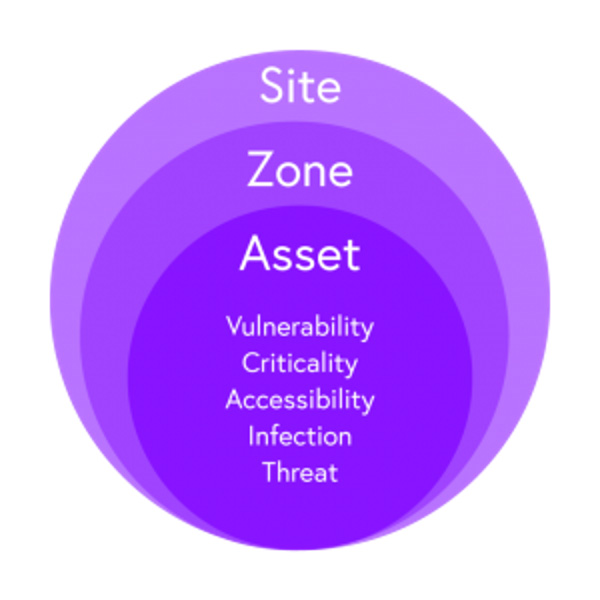
Claroty’s risk-scoring capabilities provide users with nuanced risk assessments for individual assets, virtual zones, and entire industrial sites.
To empower users with a holistic understanding of risk within their industrial environment, Claroty complements its asset-level risk-scoring capabilities with the ability to assess risk across all assets within a virtual zone or—even more broadly—across an entire industrial site.
By nature, risk management involves trade-offs: no organization has the resources, bandwidth, or permissible downtime necessary to fully mitigate every risk it faces. This is especially true when managing risk within industrial technology environments, in which low tolerance for downtime is at odds with the often-disruptive nature of patching. As such, it’s crucial for teams to be able to discern vulnerabilities (or other potential security weaknesses) which need not be prioritized from those which must be mitigated using compensating controls, either indefinitely, or until maintenance windows allow for patching.
Effectively setting these priorities requires decision-makers to have a grasp on how a potential attack against their industrial environment could play out. Claroty CTD supports this need with its Attack Vector Mapping capability, which simulates every possible type of communication along the various pathways through which an adversary could compromise a given network, leveraging criteria developed by Claroty’s decorated team of industrial cybersecurity researchers. Armed with a visual representation of how potential attacks could play out, along with contextual details explaining why particular attack chains have been identified, Claroty users can prioritize remediation based on contextual intelligence gleaned directly from the environment they’re tasked with protecting.
After forming an understanding of the risks present within your environment and setting priorities to focus on the risk factors most critical to your operations, the next step is to move forward with the appropriate actions to mitigate those risks. In many cases, the process of identifying potential attack patterns with Attack Vector Mapping will help inform this effort by helping teams zero in on vulnerable communication flows where traffic should be subject to additional verification or other compensating controls until a patch can be administered.
In addition to—or in certain situations, in place of—implementing specific compensating controls to address specific vulnerabilities or attack patterns, a growing number of industrial cybersecurity practitioners are adopting the Zero Trust model, widely known as an IT-security principle, but also highly effective in an OT context. Zero Trust dictates that all users—whether internal or external—must be continuously verified and authenticated, while only being able to access the authorized assets, applications, and data necessary to do their job. By adopting Zero Trust principles to help secure their industrial environment, companies can drastically reduce the risk of users—internal or external, unintentional or malicious—taking actions that threaten the safety, reliability, and availability of industrial environments.
Claroty Secure Remote Access (SRA) enables companies to embrace Zero Trust in an efficient, user-friendly manner by supporting capabilities and principles such as Security Assertion Markup Language (SAML), the principle of least privilege, password vaulting, and strong role-based access controls. The combination of these capabilities grants administrators complete discretion and flexibility when it comes to implementing and enforcing authentication policies, while providing users with a streamlined experience that does not affect their ability to do their job.
Be the first to hear the latest developments in the cyber industry.