Share this article on:
Powered by MOMENTUMMEDIA
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Most Cyber Security is applied around a Client/Server application by preventing access to the domain in which it exists. This works most of the time; but the consequences when security fails, can be catastrophic. The usual approach is to add more checks, or install more packages, thereby ‘strengthening’ the defences.

This approach has one major flaw: the domain is usually attached to the Internet and the Internet is the medium through which the threat is exercised. The approach does nothing to reduce the hazard of having the Internet attached.
Net-2-Core technology is different: it protects from the inside. The security is embedded within a Client/Server application and bans the Internet from access to the critical part of any Application; the database.
The method relies upon separating a Client/Server application into two parts:
Net-2-Core technology joins the two parts so that -
How does that work?
Net-2-Core uses ‘Transactions’, a Communication Database and (preferably) a LAN to link the ‘Net’ and the ‘Core’ systems.
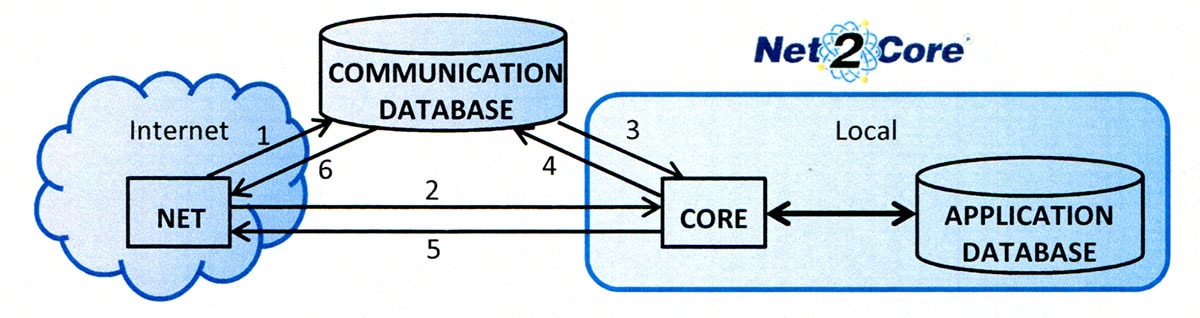
The ‘Net’ records a Transaction on the Communication Database (1) and the ‘Core’ reads the Transaction (3), executes the requirement, and places the result back on the Communication Database (4). The ‘Net’ accesses the result (6), and the Client/Server application continues.
Which leaves a few problems to be addressed:
The ‘Core’ is a stand-alone program which is not memory resident. It is loaded upon ‘Demand’ by the ‘Net’ (2). Multiple ‘Core’ programs exist simultaneously: one for every ‘Demand’ that is in progress at a point in time. The ‘Core’ is compiled VB6 code and loads for less than 2 seconds for each ‘Demand’.
Part of the ‘Demand’ provides the Key to read the Transaction on the Communication Database (3). This Key is also used to identify the result (4) and the ‘Core’ notifies the ‘Net’ (5) when it terminates and unloads. The ‘Net’ can then access the result (6).
The Key is only used by the “Core’ program to process the request for which the ‘Core’ was loaded and the ‘Net’ knows the Key it used in the ‘Demand’ and can therefore access the result. Each active request requires a different Key.
This Net-2-Core, two factor approach strengthens the isolation of the ‘Core’ from the Internet. It is a variation on two factor authentication.
Incorporating Net-2-Core into an existing Client/Server application is not overly complex.
At the most basic level, the Transactions can be fully formed, database access statements. In this approach the Results would be whatever the Application currently receives as a result of the statement. This can be applied in one common interface which replaces the call to the current database ‘provider’ software.
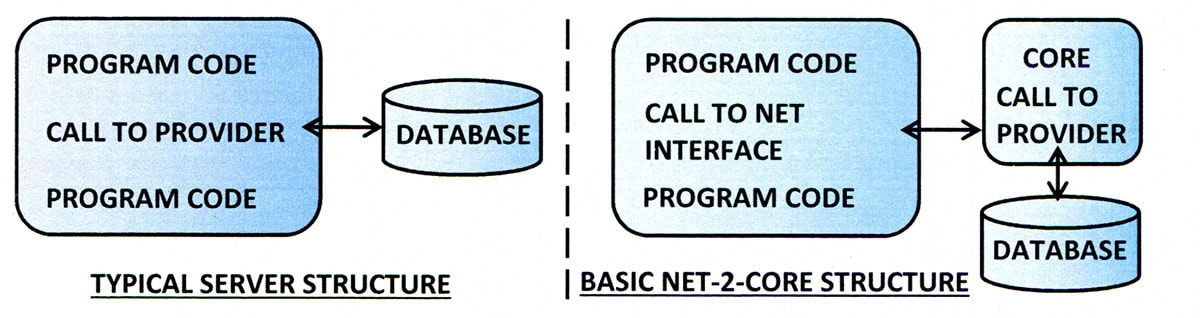
The ‘Core’ program would be constructed to apply the statements to the Application database and return whatever the result would normally be.
The common interface would then return the results to the initiator of the ‘Demand’.
This basic approach can be enhanced by -
The Enigma IDE adds many advantages around the Net-2-Core technology. It -
Creation of each of the parts ensures that the ‘Core’ will only process Transactions from which it has been created and the ‘Net’ will only process Results that it expects.
Additionally the IDE -
Net-2-Core is an enhancement to current Cyber-Security strategies. It is not a replacement.
But when the current strategies fail, as history shows they inevitably will, wouldn’t it be reassuring to know that your database is still protected.
Chris Hillman
Chris is CEO and Lead Developer of Parametric Systems.
Be the first to hear the latest developments in the cyber industry.