Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Tens of thousands of individual and enterprise-level AnyDesk customer details were recently posted for sale on a Russian-language hacking forum.
Remote desktop application company AnyDesk disclosed that it had fallen victim to a data breach late last week, and now it appears AnyDesk login credentials are circulating for sale online – probably harvested from a different hacking campaign.
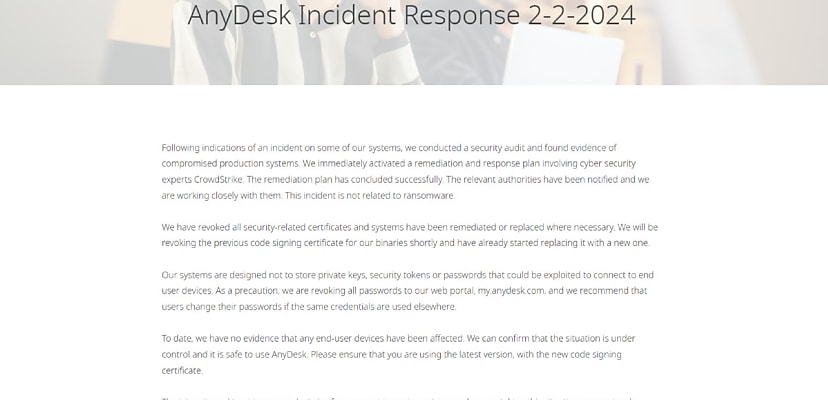
AnyDesk released a security advisory regarding “compromised production systems”, revoking all passwords and recommending users change any passwords reused elsewhere in the wake of the incident.
“Our systems are designed not to store private keys, security tokens or passwords that could be exploited to connect to end-user devices. As a precaution, we are revoking all passwords to our web portal, my.anydesk.com, and we recommend that users change their passwords if the same credentials are used elsewhere,” AnyDesk said in its advisory notice.
However, the next day, multiple hackers on the Russian-language Exploit forums – which is a clear web site – were selling sets of email addresses and passwords to AnyDesk’s login portal. One forum user was selling more than 18,000 sets of credentials for the asking price of US$15,000 in cryptocurrency.
Worse, according to security researchers at Resecurity, when they contacted the hacker, the individual was able to share screenshots of them successfully accessing AnyDesk’s login portal a full day after the company had said it was resetting passwords due to the 2 February incident.
“This suggests not all customers have still not changed their access credentials, or this mechanism was still ongoing by the affected parties,” Resecurity said in a 4 February blog post. “Undoubtedly, the complexity of deploying proper remediation measures is more significant when servicing a large customer base, and such procedures may not be instantly executed, requiring proper planning. For example, this exact scenario could be leveraged by the threat actors concerned about losing previously acquired access. Therefore, proper planning and threat modelling are necessary evils for effective remediation programs.”
The researchers believe the credentials were gathered via a separate info-stealing campaign and are now being put up for sale before they are affected by AnyDesk’s mitigation efforts following the 2 February attack.
The 2 February attack appears to have targeted AnyDesk’s production environment, and there are media reports that source code and code signing keys were successfully exfiltrated.
“We have revoked all security-related certificates, and systems have been remediated or replaced where necessary,” AnyDesk said on 2 February. “We will be revoking the previous code signing certificate for our binaries shortly and have already started replacing it with a new one.”

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.