Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Employee details and medical records were shared as proof of hack of a Victorian car dealership.
The Trigona ransomware gang has posted details of what appears to be a successful ransomware attack on a Melbourne car dealership.
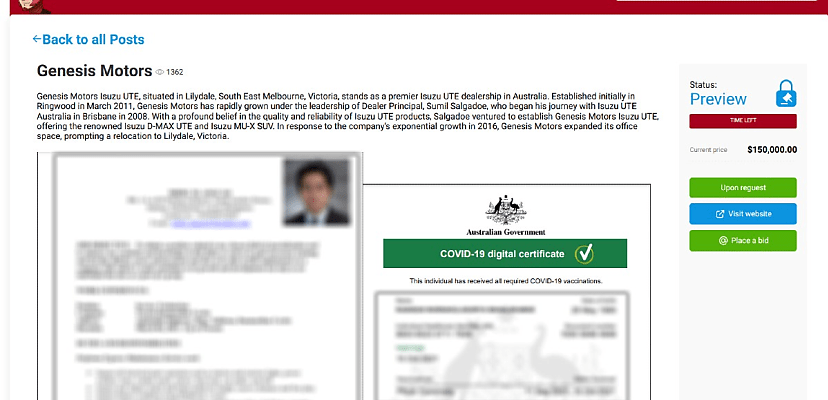
The gang posted a limited set of proof-of-hack documents on its darknet leak site on 30 January belonging to Genesis Motors Isuzu. Though it did not share the details of how much data it exfiltrated, the data it does have is up for auction, with a starting price of US$150,000.
This suggests that Trigona is using the threat of auction to pressure the victim into buying back its data or that Genesis Motors Isuzu is expected to bid for access to its data along with everyone else interested in the data.
“By acquiring this company’s confidential data, you will get access to valuable information that can help you grow your business,” a Trigona spokesperson said in the leak site post. “You will learn about the company’s strategies, strengths, weaknesses, opportunities and threats. You will also discover the needs, pain points, motivations and behaviours of its customers. You will be able to use this information to create better products and services, target the right prospects, craft compelling sales pitches and close more deals.”
The preview post includes several documents belonging to foreign nationals employed by Genesis Motors Isuzu, including a résumé, an Overseas Student Confirmation-of-Enrolment form, a valid passport and driver’s license, and a bank statement belonging to the car dealership.
Trigona – ironically named after a family of stingless bees – was first observed in action in May 2023 and has been responsible for 19 attacks since then. While far from prolific, the gang has drastically upped its operational tempo since the beginning of 2024.
In 2023, the gang was responsible for nine ransomware incidents, but in January 2024, it had already posted the same amount of victims. At the same time as it posted details of its Genesis Motors Isuzu hack, it also shared details of three others: CMG Drainage Engineering and Daher Contracting in the US and Ausa in Spain.
The group is known to gain initial access via a vulnerability in Zoho ManageEngine ADSelfService Plus or via purchasing direct access via a broker.
Cyber Daily has reached out to Genesis Motors Isuzu UTE for comment.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.