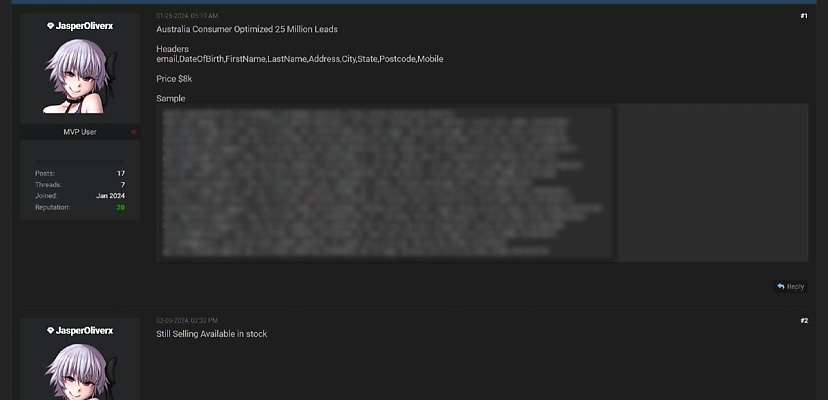
As January came to a close, an enterprising member of one of the more popular clear web hacking forums offered up quite the deal.
In a simple post, the user – JasperOliverx – promised a list of 25 million Australians complete with emails, names, dates of birth, mobile numbers, and even addresses.
“Australia Consumer Optimized 25 Million Leads,” was the header of the post, and JasperOliverx said much the same thing in the post’s body. However, Jasper also included a short sample of 16 lines of data.
Sixteen people whose details were now very public and part of a list that the apparent hacker was selling for the grand price of US$8,000.
There’s no doubt this is a huge list. Australia’s population is only just shy of 27 million, so that’s pretty much every person in the country. But, when you think about it, that number seems just a bit optimistic. If you ignore the under-four cohort, that means this list is almost everyone in the country.
Given the number of high-profile, high-number leaks and breaches that have happened in the last few years, it is close to technically possible, but it feels highly unlikely. But could all this come from just one giant data breach?
As the post said, this is an “optimised” list of “leads”, which means no, this is not a new data breach or leak, and no, it is probably not practically the entire country.
So what is this list, and where does it come from?
Great leaks of our time
Some quick analysis of the emails shows that all sixteen are legitimate and belong to real people, so this is certainly the real deal. The addresses appear to be mostly accurate, too.
What the seller means by optimised, however, is that they – or someone they are posting on behalf of – has patiently gone through the details of dozens of previous data breaches and collated this one master list. This person has formatted the details in a consistent manner, making it relatively easy to navigate, and maybe even did some research to make sure each entry was valid.
Does that add up to US$8,000 in value? That’s harder to say, but so far, only one person has replied to the post, and then only after the seller replied themselves, saying the list was “still selling” and “available in stock”.
But just the 16 lines of sample data represent a who’s who of data breaches – 36 of them, in fact. And with Troy Hunt’s excellent HaveIBeenPwned website, we can check where each email has been previously leaked online.
The earliest leak this new sample dataset comes from is a 2013 Adobe data breach, when a massive 153 million user accounts were breached alongside very poorly encrypted passwords and even password hints. It’s worth noting that those password details are not included in this optimised list.
The most recent data breach, though, isn’t even a breach per se – it’s a list of 200 million emails and other data scraped from Twitter in 2023.
In both of those cases, only one email appeared in each breach, but in many cases, most of the 16 sample emails were all involved in multiple breaches. Just three emails in the list appear in a single breach, while one poor Aussie’s email shows up in 14 discrete data breaches!
Most of the emails listed, though, are somewhere in the middle, appearing in between two and five previous leaks, while only two of the emails appear to be unique – that is, they are not listed as part of a previous leak on HaveIBeenPwned. These could come from leaks that are not yet listed, though it is also possible that the individuals have asked that their emails be opted out of HaveIBeenPwned’s database.
But I’d suggest that’s a touch unlikely. Regardless, here’s a list of just some of the data breaches these personal details – bar the two unique ones – come from and when they occurred.
MyFitnessPal
Calorie and exercise tracker MyFitnessPal had 144 million emails and more exposed in 2018, and the list has been widely circulated since. Three of the sample emails from this list of 25 million are part of this list.
Tuned Global
In January 2021, customer details from the music streaming solution were part of a list of 985,000 details posted to a hacking forum. Two of our sample emails were part of this breach.
FlexBooker
This online booking service had 3.7 million of its user accounts shared as part of a data breach in 2021. One of our sample emails was exposed in this breach.
Houzz
In 2018, interior design website Houzz – which has a global and Australian website – fell victim to a data breach that saw 144 million unique emails and other details shared on the darknet. Two of the 16 sample emails were part of this breach.
Onliner Spambot (spam list)
This is not a single breach but rather a list of emails included as part of – you guessed it – a spambot discovered in 2017. This bot had the email addresses of a staggering 711 million people. Unsurprisingly, six of the sample emails were included in this list.
Canva
The popular design app suffered a data breach in 2019 that saw 137 emails and other details exposed. One of our sample emails was part of this breach.
Adobe
The popular software company saw 153 million of its customers’ details breached in 2013. One sample email was a part of this leak.
Anti Public Combo List
This is another compiled list of data from other sources, featuring 458 million emails and password pairs. This list was found in 2016, and according to HaveIBeenPwned, it is a popular tool for credential stuffing attacks – just like the ones some poor Aussie Taylor Swift fans have fallen victim to. Despite the size of this list, only one of our sample emails was found here.
Collection #1
This is another credential-stuffing list – and a huge one. This list, discovered in 2019, contains more than 2.6 BILLION records, with a whopping 773 of them being unique to this list at the time. Four of the sample emails our hacker friend provided are part of this list.
MyHeritage
More than 92 million customer records from genealogy website MyHeritage in 2017 were in heavy circulation on hacking forums at the time. Subsequently, two of our sample emails were part of this breach.
Oxfam
Here’s one much closer to home. In 2021, Oxfam Australia suffered a data breach that saw 1.8 million customers exposed, including limited credit card data. It was first put up for sale on a hacking forum before becoming freely available a month after the initial leak. One sample email comes from this list.
QuestionPro
In 2022, survey site QuestionPro lost 100 gigabytes of data, including 22 million email addresses – some that were generated by QuestionPro, but others belonged to real people. One of the sample emails appeared in this leak.
Verifications.io
When an email verification service gets caught in a data breach, you know it’s going to be messy, and in 2019, that’s exactly what happened. After leaving a MongoDB database unsecured and public-facing, 763 email addresses were exposed – alongside a lot of other data. Given the size of this breach, three of our sample emails were impacted.
Zynga
Mobile game developer Zynga suffered a large data breach in 2019, when 173 million emails were exposed, as well as usernames and phone numbers. Four of our sample Australians were included in this breach.
CafePress
The merchandise specialist saw 23 million of its customers exposed in a data breach in 2019. One of our samples shows up in this breach.
Data Enrichment Exposure From PDL Customer
This one is a doozy, with 1.2 billion customer records exposed, including 622 million email addresses – all left on a server left unsecured by a customer of data enrichment firm People Data Labs. Despite the massive size of this data breach, only one of our sample emails appeared in it.
8fit
Fitness outfit 8fit suffered a data breach in 2018, which ended up with 15 million customers’ details circulating on the dark web a year later. One of the sample emails appeared in this leak.
Gravatar
This is a data scrape of 167 million sets of user details, breached using a technique first shared by a security researcher but that later saw the data shared among hacking forums. One of our sample email addresses appeared in this breach.
So you get the idea – there are sixteen other data breaches where these emails show up. They were all either publicly available at the time of the breach (and are no doubt still circulating, as this new list shows) or were shared with HaveIBeenPwned by the concerned individuals who discovered them.
In time, we would not be surprised to see this 25 million list appear as a discrete dataset on HaveIBeenPwned, but as you can see in some of the above breaches, there can be quite a lag between a breach being available for private sale and then showing up for free in general circulation.
While there’s no denying that seeing lists like this circulating online is alarming, in a lot of cases, the emails and personal details you see being shared like this are not new leaks. The 25 million sets of data that this hacker is selling can no doubt be put to some malicious use, but chances are someone has already been using these details in some form or another – and could have been for over a decade now.
Data breaches are nothing new, and nor are they going to go away anytime soon. But they’re often only as dangerous as we ourselves allow them to be. Sure, the holders of our data have a duty of care to protect it, but some responsibility does fall back on the shoulders of individual users to be careful with their own information, such as enabling multifactor authentication wherever possible or making sure passwords are strong and protected by a password manager.
Regularly changing your passwords whenever you think your details may have been compromised is also strongly encouraged, but a process few people pay attention to.
And do not forget just how useful HaveIBeenPwned is for working out just how exposed you really are. Go to the site and enter your own email now. Personally, my private email appears in a truly staggering 17 data breaches and collections, based on leaks from games I’ve not played in well over 10 years, and in some cases, social media platforms I’ve not used for nearly 20!
My work email is safe, but then that address is only just over a year old. In time, it will be part of a breach as well – and it’s up to me to be aware of that and take every precaution I can.

David Hollingworth
David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.