Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Is this a mighty blow against cyber crime, or just a glancing blow? Taking out LockBit should be celebrated, but it’s just one small step in the fight against ransomware.
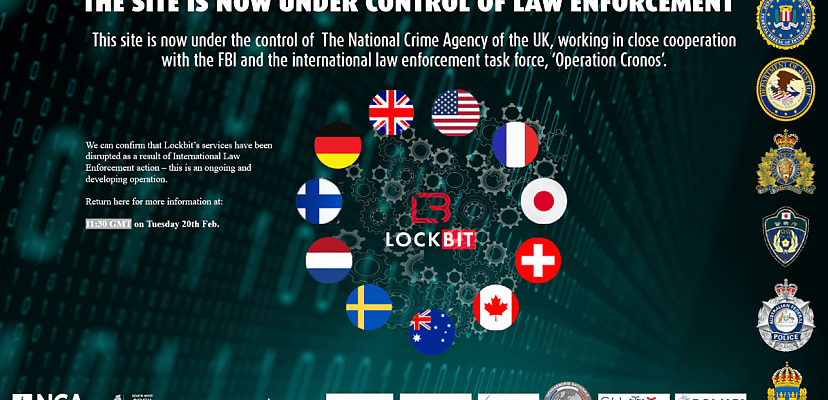
This week saw a global partnership of law enforcement agencies, headed by Europol, take down the LockBit ransomware gang.
And it wasn’t just you’re average “we’ve seized your leak site and some infrastructure” takedown. Rather, there were multiple arrests, more charges laid beside, and even a very snarky website takeover that used LockBit’s own leak site as a way to boast about just how total the takedown was.
Long story short, in internet parlance, LockBit was comprehensively pwned.
But what – if anything – happens next? What changes in the world of ransomware, and who is really hurt by the police action?
For LockBit’s affiliates – the gang sells (well, sold) its ransomware smarts to a raft of customers, taking a cut of any ransom paid – this is a rough time. They’ll be aware that LockBit’s operation has been not only disrupted but quite thoroughly taken apart. And after a handful of arrests and the apparent seizure of the gang’s infrastructure, you’d have to be worried – worried that any number of law enforcement agencies are even now sharing information on LockBit’s affiliates and where and who they are.
This leaves those affiliates with two choices – get out of the ransomware game entirely and hope for the best, or look for another ransomware-as-a-service (RAAS) provider. Those who get out of it entirely, well, that’s good news all around, and good riddance. But those who still feel the need to make money off the misery of others may find it difficult to find another operator quite as prolific as LockBit.
LockBit was no doubt a slick – as these things go – outfit. It’s been the most prolific ransomware gang by some margin for some time; just last week, it was responsible for a third of all ransomware incidents worldwide. That speaks to a huge amount of capacity, and I’m not sure there are many similar gangs ready to take up that slack.
Arguably, the two biggest RAAS operations now that LockBit is effectively off the board are Clop and ALPHV, also known as BlackCat. Clop had a signal year off the back of its MOVEit GoAnywhere supply chain attack last year. So, does it really need more customers? Criminals are generally greedy sorts, sure, but if we assume that any given group is already working as hard as it can to operate, where will these affiliates looking for a new service go to find a new partner?
As to APLHV, it’s already been taken down once. The FBI posted a takedown notice to its leak site in December of last year, but the gang was back in operation in no time – the darknet is, by design, a sneaky place. ALPHV may be willing to take advantage of the sudden influx of affiliates, but you’ve got to imagine that any RAAS operator right now might be wary of new affiliates – they could already be compromised and under law enforcement scrutiny.
Given that there are certainly actors out there simply selling ransomware suites, it’s not impossible that some affiliates may decide to cut out the middleman and form their own operations. However, affiliates turn to RAAS operations in the first place largely because they lack either the expertise or the tools to operate independently. Buying the tools is one thing; making use of them entirely is another.
That said, quite a few current ransomware operators today simply bought out the infrastructure of yesterday’s gangs, so it’s certainly possible.
Others may be using RAAS outfits because they feel keeping one step removed from the actual crime is the safest option, so for those actors, going independent may not be at all palatable.
Ultimately, the affiliates are a bit of a wildcard, but one thing I can’t imagine happening is another operator or operators stepping into what appears to be the vacuum left behind by LockBit.
Ransomware gangs operate on a stage of vast opportunity. The world is, effectively, their oyster, and different gangs operate in different capacities. I’ve heard of ransomware gangs going after each other out of some sense of competition, but when you have only 50-odd gangs operating at a global scale – it’s a target-rich environment, and while every gang would no doubt like to be as successful as LockBit, I can only surmise that manpower and technical limitations are what’s holding them back.
LockBit disappearing – for now – does not necessarily leave a vacuum that other actors will naturally fill.
But what it may do is introduce an element of caution. By all reports, law enforcement has gotten right inside LockBit’s infrastructure, and if it can happen to the gang on top, it can happen to anyone.
Will that mean things slow down? Maybe a little, and maybe at first, but given greed is the main motivator here – never believe a ransomware gang’s claims that they’re just honest pen-testers doing their victims a favour – it won’t slow down for long, I think. If these people were risk-averse, they wouldn’t have turned to international cyber crime in the first place.
Ed Williams, vice-president for Europe, Middle East, and Africa (EMEA) consulting and professional services at Trustwave, agreed.
“I will give it two to three months,” Williams said via email, “after which we’ll see a reincarnation of this flavour of ransomware, which I suspect will be even more sophisticated as the threat actors will have taken lessons from today and be able to cover their tracks better going forward”.
ALPHV’s apparent resurrection shows us that takedowns are not necessarily permanent in this field after all.
And that’s ignoring entirely the fact that the success of ransomware operators isn’t just down to their technical skill. Shutting down a few servers and making some arrests is great, believe me, but it’s not going to change the key factor that makes ransomware tick, according to Williams.
“Why? Because the recent law enforcement activity does not remediate the root issues that LockBit exploits,” Williams said. “Organisations continue to ignore basic cyber hygiene and aren’t prepared not only for an attack, but for incident response and recovery.”
“Over the longer term, however, I suspect it’ll be business as usual. After all, we have seen other major threat groups taken offline, only to see them pop back up.”
We should absolutely celebrate this achievement. But we should also be aware that stopping one gang is, sadly, not going to make ransomware go away overnight. It’s a long road ahead, and the long arm of the law actually only goes so far.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.