Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Another new ransomware operation has sprung up, this time one that is only after one thing – Mogilevich just wants your money.
UPDATE 3/3/24: A Mogilevich spokesperson has said that the whole operation was a money-making scam - it's not a ransomware operation at all.
The ransomware group calling itself Mogilevich claimed its first victim on 20 February, and it was quite a statement.
The newly formed group was claiming to have 22 gigabytes of data belonging to Infiniti USA, part of the luxury car division of automotive giant Nissan, including customer information that included VIN details, names and addresses, and emails and passwords.
Days later, Mogilevich declared the data had been sold – more on that later. Since then, on 26 February, the gang claimed its second victim: global user-generated content firm Bazaarvoice.
It’s worth noting that as this article was being written – overnight, in fact – Mogilevich claimed to have two more victims: Ireland’s Department of Foreign Affairs and video game company Epic Games.
That data has, as of the time of writing, not been sold, and like Infiniti USA, it’s available to whoever would like to purchase it.
So, who is this newest kid on the ransomware block, and what makes them tick?
The first giveaway may be in the name. Mogilevich is a Russian name and is, in fact, the name of a Ukrainian-born Russian crime boss – Semion Yudkovich Mogilevich. The 77-year-old Mogilevich was dubbed “the most powerful and dangerous gangster in the world” by the FBI and is known by many European law enforcement agencies as the “boss of all bosses”. Suffice it to say, he’s probably the kind of role model a ransomware gang might have – especially a Russian one.
It also might just be a cool-sounding name, too, as a possible translation is Grave’s Son. Kinda goth, but no doubt cool-sounding to a gang of hackers.
Regardless, the name could mean the group is Russia-based, or at least based somewhere in that part of the world – or it could just be colour to put researchers off the scent. That said, it does appear that English is not the group’s first language.
Mogilevich seems to be far more confident in its identity and aims than the last new group we looked at, Trisec. The group has a plain but functional darknet leak site, as well as a Telegram channel – though the latter may already be abandoned. It also eschews fancy logos and avatars – Mogilevich is all business.
And that business is very much making money from ransomware.
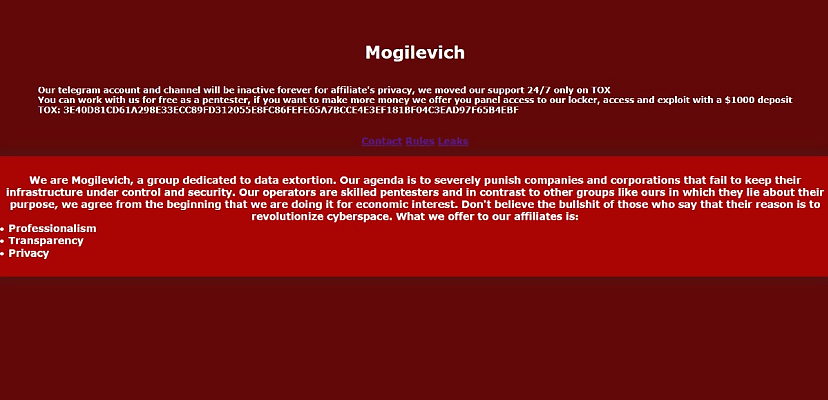
“We are Mogilevich, a group dedicated to data extortion,” the gang said in its first post on 18 February.
“Our agenda is to severely punish companies and corporations that fail to keep their infrastructure under control and security.
“Our operators are skilled pen-testers and in contrast to other groups like ours in which they lie about their purpose, we agree from the beginning that we are doing it for economic interest.”
The group also hires itself out to affiliates looking to make a buck, but only if they put money down first.
“You can work with us for free as a pen-tester, if you want to make more money, we offer you panel access to our locker, access and exploit with a $1,000 deposit,” the group said at the top of its leak site, alongside details of how to make contact via the secure messaging app Tox.
Mogilevich also claims that it expects affiliates to operate via a strict set of rules, which includes staying away from critical infrastructure, such as hospitals, and always asking for permission before making any decisions. The group also notes that affiliates are allowed to talk to journalists, so long as there are “appropriate requests”.
The group was also advertising on its Telegram channel for affiliates, but Mogilevich seems to have ditched Telegram. The group’s channel was listed on its leak site originally, alongside Tox and a mail2tor.com email address, but those last have now been deleted, with the leak site now warning users of its site that Tox is the only way to contact Mogilevich.
“Warning, this is the only contact information we have, if you find people with the same name as us on different platforms than those listed, they are simply impersonating, and it is advisable to verify our domain first,” Mogilevich’s site now said.
What can be inferred from this? Well, apart from a healthy and no doubt justified level of paranoia, not much. The last post on the Telegram channel was on 25 February, when it declared that the Infiniti USA information had been sold.
“Mogilevich Group here, we would like to inform you that the data of the following company: infinitiusa.com have been sold, and I would also like to say that it would have been better to have paid the ransom,” the post said. “We have no time to waste, new corporations will be added to our blog soon.”
It sounds like someone other than Infiniti USA or Nissan bought the data, which could lead to further attacks on the company down the line, depending on what was actually in the leak. The gang could be trying to scare its victim by faking the sale of the data, especially if negotiations have failed and the gang thinks it might be able to twist the knife a little further. But it seems a cheap tactic for what appears to be an already technically proficient operation.
It’s also entirely possible that the gang isn’t a ransomware group at all but rather opportunistic scammers hoping to either trick someone into buying fake data or some poor company into paying a ransom when they weren’t even hacked. However, if that is the case, Mogilevich is very optimistic in its targeting – we can’t see a government agency or a global gaming giant falling for such a scam.
And since Epic denied has now denied that any cyber attack has taken place on its network, maybe that's exactly what Mogilevich is - a scam operation. The group has been unable to reveal any evidence of its activity, either to Epic or to Cyber Daily.
We’ll be keeping an eye on both Mogilevich’s leak site and its Telegram channel, in case it is still in use, to see what else we can learn about this new group.
One thing we can say for sure is that Mogilevich appears to be one very serious ransomware gang.
Sadly, we’re also sure we’ll hear more from them shortly.
UPDATE: Edited on 29/02/24 to add further thoughts on Mogilevich being scammers

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.