Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
The Black Basta ransomware gang has posted details of a hack affecting nearly a dozen Australian organisations.
A ransomware gang has posted dozens of Australian passports and driver’s licenses to the dark web after apparently compromising a cloud-based hosting service.
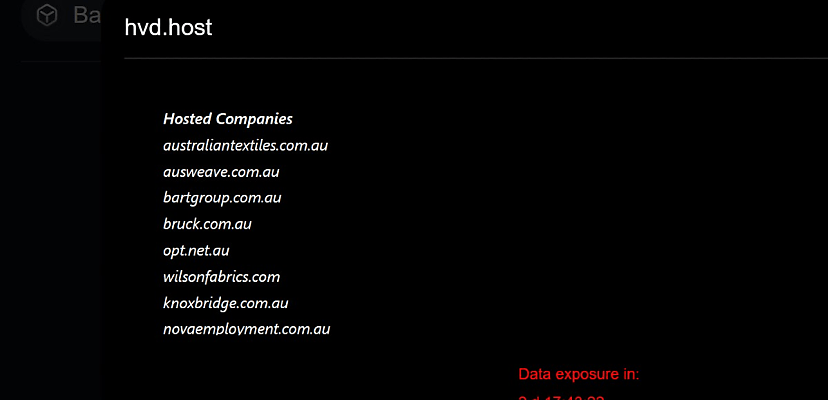
The Black Basta gang has not disclosed who the hosting service is; however, referring to the victim only as “hvd.host”.
What the gang has shared, however, is a list of mostly Australian businesses whose data the gang is threatening to publish if a ransom isn’t paid by 9 March. Thirteen companies are listed by the gang.
Black Basta listed the companies by their websites as follows:
australiantextiles.com.au
ausweave.com.au
bartgroup.com.au
bruck.com.au
opt.net.au
wilsonfabrics.com
knoxbridge.com.au
novaemployment.com.au
primrose.co.uk
xenit.com.au
advancedcs.com.au
therose.pub
localbar.com.au
Several of the listed websites are not currently active.
Black Basta has also shared passport scans, scanned driver’s licenses, and a scanned Medicare card. Some documents are expired, but a large number are still valid. At least some of the scanned documents belong to past and present employees of one of the companies listed by Black Basta – Optimum Health Solutions.
The gang also shared a screenshot of a file directory with folders labelled ACS, ATM, AW, LB, OHS, ONC, and WF. Several subfolders appear to belong to The Local Bar.
Black Basta claims to have about 700 gigabytes of data in total, including account details, financial data, “personal employee documents”, legal documents, and more.
Where possible, Cyber Daily has sought comment from all the listed victims, including Optimum Health Solutions.
Black Basta has been in action since at least April 2022 and operates under a ransomware-as-a-service model, hiring its technical nouse out to other hackers to employ. It is a highly active outfit, with its affiliates racking up more than 40 victims in 2024 alone.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.