Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
International cyber agencies have banded together to release a new advisory on an infamous cyber gang after it reeled in over US$42 million in ransomware payments in less than its first year.
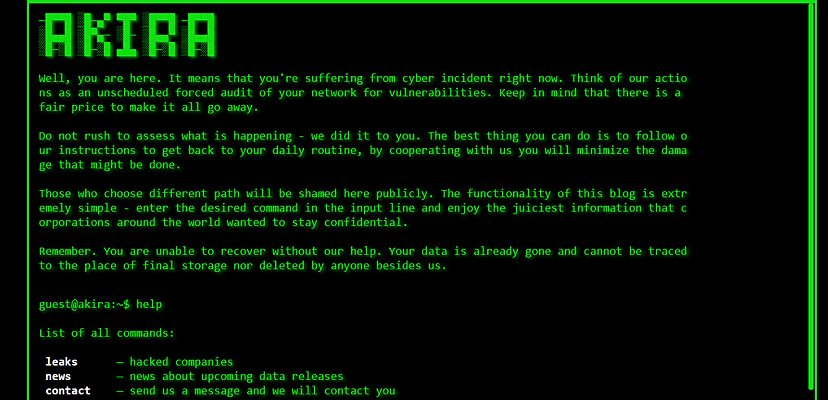
The FBI, along with the Cybersecurity and Infrastructure Security Agency (CISA), Europol’s European Cybercrime Centre (EC3), and the National Cyber Security Centre in the Netherlands (NCSC-NL), have released a joint advisory on the Akira ransomware gang.
Akira, which first appeared in March 2023 targeting Windows systems before establishing malware for Linux systems in April, had reportedly earned itself roughly US$42 million in ransoms from over 250 companies by 1 January 2024, according to the advisory.
“Since March 2023, Akira ransomware has impacted a wide range of businesses and critical infrastructure entities in North America, Europe, and Australia,” said the advisory.
“As of January 1, 2024, the ransomware group has impacted over 250 organisations and claimed approximately $42 million (USD) in ransomware proceeds.”
Alongside its large earnings, Akira has a portfolio of sizable and reputable victims, including Lush Cosmetics, Gansevoort Hotel Group, and Nissan Australia, the latter of which affected over 100,000 people.
The group’s malware was originally written in C++, and the files it encrypted would receive the .akira extension; however, this changed in August 2023 when the group began using the Rust-based Megazord, which encrypts files with the .powerranges extension. Both malware types are still being used.
The joint advisory recommends that organisations implement a number of mitigations to prevent Akira from successfully breaching and encrypting systems, including implementing a recovery plan with maintained backups of sensitive data and servers, requiring passwords and multifactor authentication, segmenting networks, keeping software and firmware up to date, identify and detect abnormal activity with a monitoring tool, disabling hyperlinks in emails and command-line and scripting activities and permissions and much more.
Akira’s rapid rise to success could be explained by beliefs that it stemmed from the now-defunct Conti Ransomware gang, with which it shares some similarities.
The Conti ransomware group began operation in 2020, operating a ransomware-as-a-service model. The group was known for targeting healthcare organisations, particularly in New Zealand.
The group began to fall apart during Russia’s invasion of Ukraine, when Conti came out publicly supporting Russia and its aims. However, soon after, an unknown individual quickly leaked large volumes of chat logs and the group’s source code in protest. The leaked messages laid open the group’s operations and possible links with the Russian FSB.
The group disbanded weeks later.
The code used by Akira in its 2023 operations significantly overlaps with Conti’s source code, and Akira uses the same list of file exceptions when it comes to encryption.
Researchers have also noted an overlap in the cryptocurrency wallets used by the two groups.
“In a pattern analysis of cryptocurrency wallets, researchers were able to identify overlap in the wallets between Akira and Conti,” the report read. “In two of these transactions, the wallets had previously been affiliated with Conti’s leadership team.”

Be the first to hear the latest developments in the cyber industry.