Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
The FBI is inviting victims of the LockBit ransomware gang to reach out after it secured 7,000 decryption keys from the threat group.
During a keynote at the 2024 Boston Conference on Cyber Security discussing its ongoing disruption of LockBit, a procedure known as Operation Cronos, FBI cyber division assistant director Bryan Vorndran revealed that 7,000 keys had been secured.
“We now have over 7,000 decryption keys and can help victims reclaim their data and get back online,” said Vorndran on Wednesday (5 June).
“We are reaching out to known LockBit victims and encouraging anyone who suspects they were a victim to visit our Internet Crime Complaint Center at ic3.gov.”
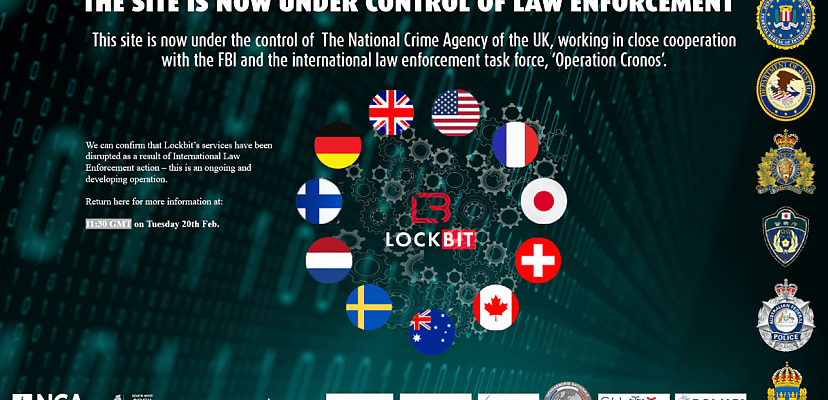
Operation Cronos first came to light in February when the FBI alongside global law enforcement agencies from the UK, Germany, Canada, and Australia seized the group’s dark web leak site.
“This site is now under the control of The National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, ‘Operation Cronos’,” the sites now say.
“We can confirm that LockBit’s services have been disrupted as a result of international law enforcement action – this is an ongoing and developing operation.”
Following this, law enforcement gave the group a taste of its own medicine, leaking the threat group’s source code and some internal information on its own leak site while releasing decryption keys to victims.
Despite this, LockBit was back up and running later that month and returned with a vengeance, listing major organisations like London Drugs and OracleCMS, the latter of which led to organisations and agencies using OracleCMS being breached, such as Nissan Oceania, a number of Australian councils and more.
Vorndran’s keynote provided an analysis of Operation Cronos and its findings,
“LockBit was set up by a Russian coder named Dmitry Khoroshev,” he said.
“He maintains the image of a shadowy hacker, using online aliases like ‘Putinkrab,’ ‘Nerowolfe,’ and ‘LockBitsupp.’ But, really, he is a criminal, more caught up in the bureaucracy of managing his company than in any covert activities.”
Khoroshev was sanctioned by the US, the UK, and Australia, and according to Vorndran, began offering up his competitors in the hopes of a softened blow from the FBI.
“Khoroshev then tried to get us to go easy on him by turning on his competitors, naming other ransomware-as-a-service operators,” said Vorndran.
“So, it really is like dealing with organised crime gangs, where the boss rolls over and asks for leniency.
“We will not go easy on him.”
The FBI also discovered that LockBit and its affiliates were keeping stolen data after being paid ransom by its victims, despite telling them they had deleted it.

Be the first to hear the latest developments in the cyber industry.