Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
The ransomware landscape demonstrates its dynamic and rapidly shifting nature, as evidenced by the marked increase in incidents and impact during the second quarter of 2024.

Despite declining incidents and the relatively low impact of ransomware attacks in Q1, this second quarter has shown a significant resurgence.
This recovery is particularly notable given major ransomware groups’ initial setbacks due to law enforcement operations in Q1. While these initial disruptions had temporarily curtailed the activities of several leading ransomware groups, the number of ransomware attacks almost doubled in Q2 compared to Q1, causing significant operational disruptions to industrial organisations.
Both the resilience and adaptability of ransomware groups highlight their persistent threat to industrial sectors, including a notable shift in the ransomware-as-a-service landscape, with groups like BlackSuit and RansomHub emerging with updated tactics and techniques. These updates include more sophisticated encryption algorithms, improved lateral movement methods within networks, and more effective evasion of detection mechanisms.
Critical industrial operations are the prime target of ransomware activity
The industrial sector remains a prime target for ransomware groups due to the critical nature of its operations and the potentially high impact of disruptions, with ransomware groups focusing on high-impact operators to maximise their profits. The risk posed by ransomware is further exacerbated as government-affiliated groups adopt ransomware tactics, and hacktivists increasingly utilise and even build their own ransomware tools, illustrating the convergence of ideological and financial motivations in the cyber threat landscape. This growing trend proves the evolving and escalating nature of the ransomware threat, which spans beyond traditional cyber criminal enterprises to include politically and ideologically driven adversaries.
In Q2, Dragos’ assessment of ransomware attacks with increased business impact against industrial organisations was validated, with incidents exhibiting more severe impacts than in earlier quarters. This quarter saw a significant rise in the frequency and severity of attacks, reflecting the evolving threat landscape and the persistent risk posed by ransomware groups. For example, in May, Frontier Communications was hit by RansomHub, resulting in a shutdown of certain systems, resulting in material operational disruption.
Current ransomware trends, patterns, and observations
Globally, Dragos continues to analyse ransomware variants used against industrial organisations, tracking ransomware information via public reports and data uploaded or appearing on dark websites. These sources report victims that were listed as targets and those that pay or otherwise “cooperate” with the criminals, and they do not necessarily match one-to-one with all incidents that took place in this last quarter. Several notable observations from Q2 include a significant resurgence in ransomware activity and the emergence of new tactics by ransomware groups. Although we saw a decline in Q1 in both the number of incidents and the impact of ransomware attacks, there was a marked increase in Q2, with the total number of ransomware incidents almost doubled.
Among the 86 ransomware groups known for targeting industrial organisations, 29 remained active in Q2 compared to 22 in Q1. However, Q2 saw a resurgence with several rebranded groups and new entrants in the ransomware landscape. Groups such as BlackSuit (formerly Royal ransomware) and RansomHub (previously Knight ransomware) have shown notable activity, leveraging sophisticated tactics and techniques to enhance their operations.
In addition to the resurgence, the overall impact of these ransomware attacks against industrial organisations remains a significant concern. While Dragos did not identify any ransomware attacks targeting industrial control systems (ICS) or operational technology (OT) processes, ransomware groups have disrupted the IT systems of industrial organisations. Disruptions to OT networks have occurred, primarily due to the interdependencies between OT and IT systems. The rise in ransomware incidents during Q2 underscores the evolving threat landscape and the persistent risk posed by these groups.
Regional and industry impact observations
Ransomware incidents exhibited a marked increase, impacting various regions differently. North America experienced 187 ransomware incidents (approximately 60 per cent of the observed 312 global ransomware attacks), followed by Europe with 82 incidents or approximately 26 per cent. Asia experienced 10 per cent of global ransomware incidents (29 incidents reported), and South America with 2 per cent of global ransomware incidents (six incidents). Middle East, Australia, and Africa had approximately 1 per cent each of the global ransomware incidents, with just eight incidents reported collectively.
The manufacturing sector was the most affected, with 210 observed incidents, or approximately 67 per cent of all ransomware incidents, and ICS experienced 47 incidents or 15 per cent of the total incidents. The transportation sector was impacted 23 times (7 per cent), followed by government entities, oil and natural gas, communications, and mining, electric, renewables, and water. In addition to the primary industries and sectors, Dragos observed 23 unique manufacturing subsectors impacted by ransomware in Q2, with construction (33 incidents) and consumer and food and beverage (27 incidents each) the most impacted.
Ransomware groups trends, patterns, and observations
Dragos’ analysis of numerous ransomware data from Q2 indicates that the LockBit group was behind most attacks against industrial organisations, with approximately 21 per cent (or 66 incidents) of observed ransomware events. The Play ransomware was second, with approximately 10 per cent (or 31 incidents).
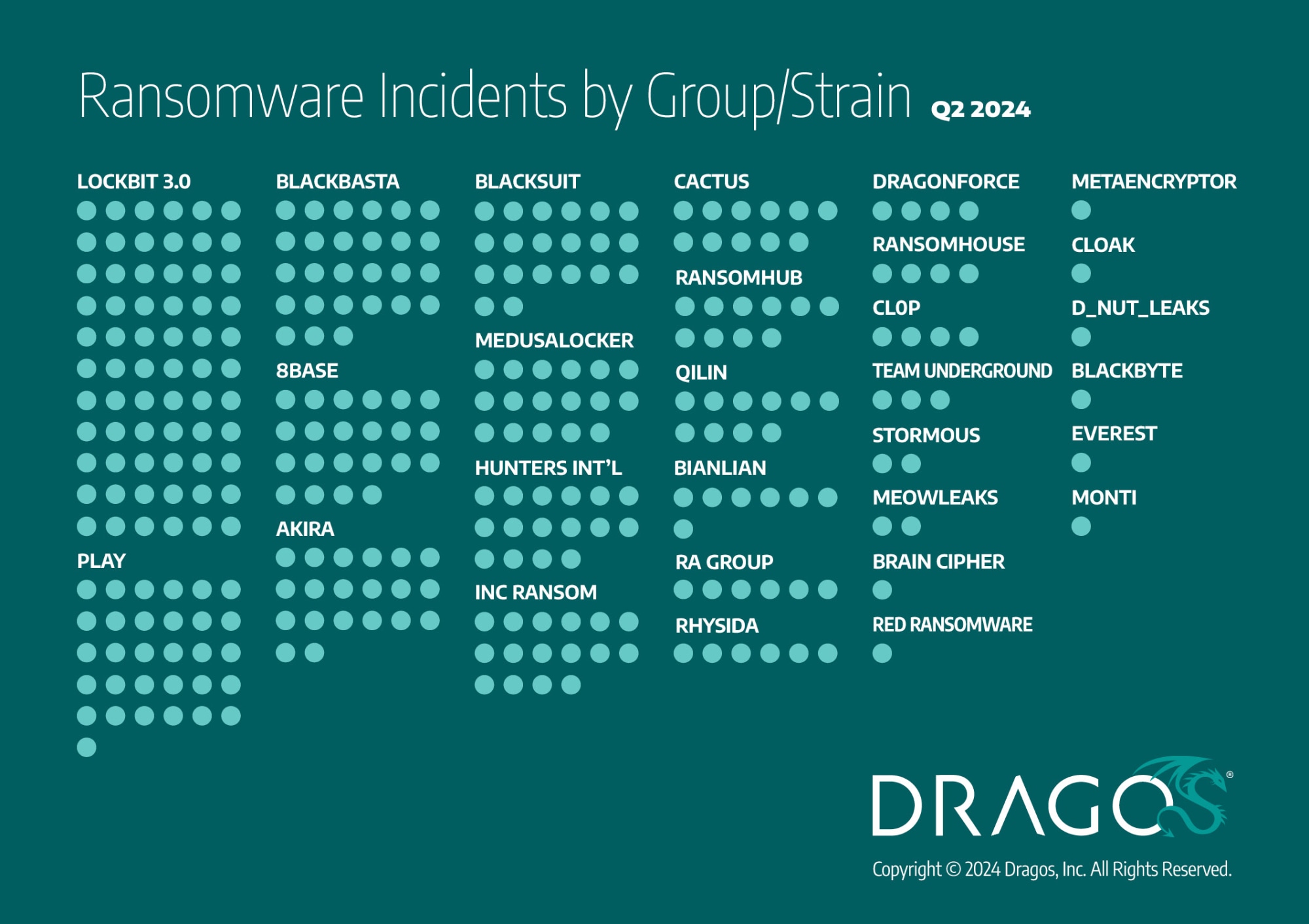
Ransomware incidents by ransomware group, Q2 2024
Dragos observed the activity of 12 ransomware groups in Q2 that were not active or observed in Q1, such as RA Group and DragonForce. Their Q2 presence highlights the evolving nature of ransomware group activities and the constant shifts within the ransomware ecosystem.
Looking ahead
Ransomware groups will continue to refine their operations, leveraging sophisticated methods such as zero-day vulnerabilities to enhance their attacks. Dragos assesses with moderate confidence that the ransomware threat landscape will continue to evolve, characterised by the introduction of new ransomware variants and increasing coordinated campaigns targeting industrial sectors. Despite significant law enforcement actions, the observed resilience and adaptability of ransomware groups indicate a likely continuation of this trend.
While Dragos did not identify any ransomware attacks directly targeting ICS/OT processes, the interconnected nature of IT and OT environments means that disruptions to IT systems can have significant downstream effects on OT operations. This interdependency suggests that ransomware groups may increasingly target OT networks to amplify the impact of their attacks, potentially compromising the safety and operational integrity of industrial organisations. A more detailed Q2 analysis is available here.
Be the first to hear the latest developments in the cyber industry.