Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
CISA and other US agencies have released an advisory detailing RansomHub’s ransomware operations and tactics.
The US Cybersecurity and Infrastructure Security Agency (CISA) released a detailed report on the operations of the high-profile – and high-volume – ransomware gang, RansomHub, overnight.
The FBI, the Multi-State Information Sharing and Analysis Center (MS-ISAC), and the Department of Health and Human Services (HHS) also worked on the advisory.
In some ways, it’s an impressive achievement – RansomHub has only been active for around six months, but some of the most influential law enforcement and cyber security agencies are already very much paying attention.
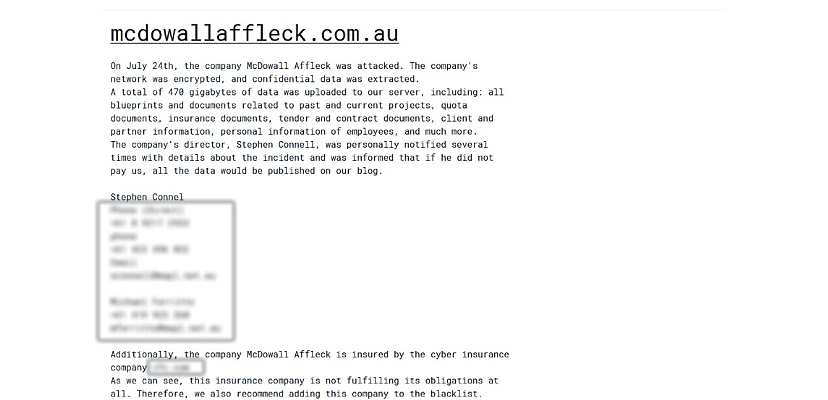
As CISA and its partners note, the gang has already clocked up 210 victims – and possibly more, given that some victims have likely paid their ransoms and not been listed on the gang’s dark web leak site.
So who is RansomHub?
The gang is likely the successor to the Knight ransomware operation, which itself was a successor to the Cyclops ransomware gang. While RansomHub feels like a new operation, it’s built on solid foundations that go back to at least May of 2023.
It’s also a ransomware-as-a-service operation, with affiliates using RansomHub’s ransomware to attack targets that they have already compromised. One of the reasons for RansomHub’s high rate of attacks is that – according to CISA – several “high-profile affiliates” have migrated to RansomHub from the LockBit and ALPHV ransomware operations.
Given both of the latter gangs have experienced their own high-profile run-ins with international law enforcement operations, it makes sense that their affiliates might be looking for what appears to be a more secure option.
RansomHub’s affiliates use a range of initial compromise methods, from phishing emails to exploiting known vulnerabilities in a range of platforms such as Citrix’s NetScaler, FortiOS, Java OpenWire, and Confluence Data Center and Server instances. Affiliates have also been observed using brute strength methods such as password-spraying accounts that were already compromised in prior data breaches.
Once inside a network, RansomHub affiliates use tools such as Angry IP Scanner and Nmap to scan the local topography, as well as living-off-the-land techniques via PowerShell. When these affiliates deploy RansomHub’s ransomware, they often rename the executable to pass as something innocuous, such as Windows\.exe or Downloads.
Once securely inside a network, attackers re-enable disabled accounts and create new ones to maintain persistence, escalate privileges, and gather further network credentials before spreading laterally throughout the network using a range of methods and tools, such as Remote Desktop Protocol and pen-testing tool Cobalt Strike.
At the same time, affiliates also use several methods to evade detection and investigation.
“The affiliates have also cleared Windows and Linux system logs to inhibit any potential incident response,” CISA said in its advisory.
“Affiliates used Windows Management Instrumentation to disable antivirus products. In some instances, RansomHub-specific tools were deployed to disable endpoint detection and response (EDR) tooling.”
RansomHub’s ransomware itself focuses entirely on encrypting a victim’s data, apparently, and not on the exfiltration of that data, so that process again depends on the affiliate behind each individual attack. Tools observed in the exfiltration process include PuTTY, various Amazon AWS S3 buckets/tools, HTTP POST requests, WinSCP, Rclone, Cobalt Strike, and Metasploit.
When the ransomware does get to work, it typically uses an Elliptic Curve Encryption algorithm – Curve 25519. This takes advantage of a public/private key unique to each victim and is even capable of stopping a wide range of processes to encrypt files currently in use as well.
“The ransomware executable does not typically encrypt executable files. A random file extension is added to file names, and a ransom note generally titled How To Restore Your Files.txt is left on the compromised system,” CISA said.
Then, the extortion process begins. Victims are generally given between three and 90 days to pay a ransom – depending on the affiliate – and are given a client ID and instructions on how to contact RansomHub on the darknet.
This is exactly the process that RansomHub’s half dozen Australian victims since April will have gone through.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.