Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Hackers demand 100 bitcoins within six days, or they will publish more than three terabytes of data, including passport details, Social Security numbers, passwords, and personal information.
The Port of Seattle in the United States revealed last week it had fallen victim to a ransomware attack on or around 24 August, explaining in a statement that numerous systems at both the city’s ports and Seattle-Tacoma International Airport had been impacted.
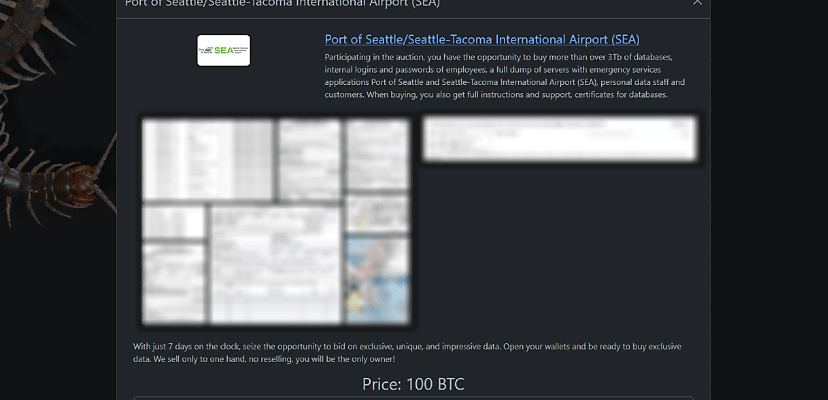
Days later, on 16 September, the Rhysida ransomware gang claimed the Port of Seattle and SeaTac International as a victim, listing several documents and details of the ransom demand.
“Participating in the auction, you have the opportunity to buy more than over [sic] 3Tb of databases, internal logins and passwords of employees, a full dump of servers with emergency services applications Port of Seattle and Seattle-Tacoma International Airport (SEA), personal data staff and customers,” a Rhysida spokesperson said on the gang’s dark web leak site.
“When buying, you also get full instructions and support, certificates for databases.”
The gang said it would publish the data within seven days (now six at the time of writing) and is demanding a 100 bitcoin ransom – approximately US$5.8 million.
“With just seven days on the clock, seize the opportunity to bid on exclusive, unique, and impressive data,” Rhsyida said in its usual boilerplate. “Open your wallets and be ready to buy exclusive data. We sell only to one hand, no reselling, you will be the only owner!”
The data posted includes a scan of a current passport belonging to a program manager at the Port of Seattle, several Request for Taxpayer Identification Number and Certification IRS forms ( complete with personal information and signatures), a form requesting an identification card (with personal information such as weight, height, Social Security number, and work and home addresses), as well as other documents too low resolution to identify.
Also included is what appears to be a detailed map of Portland International Airport.
Rhysida also posted a screenshot of what appears to be ransom negotiations between a Port of Seattle spokesperson and the gang, attempting to decrease the ransom amount.
Port of Seattle’s 13 September statement detailed the impact of the 24 August attack.
“Our investigation has determined that the unauthorised actor was able to gain access to certain parts of our computer systems and was able to encrypt access to some data. We took steps to block further activities, including disconnecting our systems from the internet, but unfortunately, the encryption and our response actions hindered some port services, including baggage, check-in kiosks, ticketing, Wi-Fi, passenger display boards, the Port of Seattle website, the flySEA app, and reserved parking,” a Port of Seattle spokesperson said.
“Our team was able to bring the majority of these systems back online within the week, though work to restore some systems like our external website and internal portals is ongoing.”
However, the Port of Seattle statement contradicts the data shared by Rhysida regarding alleged negotiations.
“The Port has refused to pay the ransom demanded, and as a result, the actor may respond by posting data they claim to have stolen on their dark web site. Our investigation of what data the actor took is ongoing, but it does appear that some Port data was obtained by the actor in mid-to-late August,” the spokesperson said.
“Assessment of the data taken is complex and takes time, but we are committed to these efforts and notifying potentially impacted stakeholders as appropriate. In particular, if we identify that the actor obtained employee or passenger personal information, we will carry out our responsibilities to inform them.”
Steve Metruck, executive director of the Port of Seattle, said in the 13 September statement that the Port of Seattle has no intention of paying the ransom.
“Paying the criminal organisation would not reflect Port values or our pledge to be a good steward of taxpayer dollars. We continue working with our partners to not just restore our systems but build a more resilient Port for the future,” Metruck said.
“Following our response efforts, we also commit to using this experience to strengthen our security and operations, as well as sharing information to help protect businesses, critical infrastructure and the public.”
Port of Seattle declined to respond to Cyber Daily’s request for clarification on Rhysida’s claims that the Port has been negotiating a ransom payment.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.