Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Ransomware gang Akira claims breach of Queensland-based transport company, saying it has employee IDs and financial data.
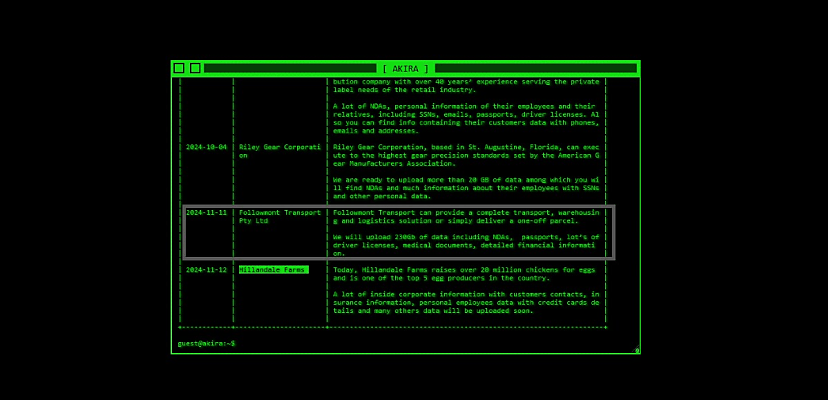
The Akira ransomware gang has claimed Queensland-headquartered transport company Followmont Transport as a victim on its darknet leak site overnight.
The threat actor claims to have stolen 230 gigabytes of data, but it has not provided a date of publication or details of its ransom demand.
“We will upload 230Gb of data including NDAs, passports, lot’s [sic] of driver licences, medical documents, detailed financial information,” the gang said in an 11 November update to its retro-themed darknet leak site.
As a rule, Akira does not share evidence of its successful hacks; however, Followmont Transport has confirmed a cyber incident has been identified.
“Followmont Transport is aware that a third party has named our company online alongside claims they have accessed some of our data,” a Followmont Transport spokesperson told Cyber Daily.
“We first became aware of the unauthorised access to our systems in October, following which we immediately notified the Australian Cyber Security Centre (ACSC) and then the Office of the Australian Information Commissioner (OAIC).”
Followmont’s systems remain “fully operational”, and the company continues to monitor its network for any further activity.
“We have been in regular contact with our staff and relevant stakeholders from the onset of this incident and have assured them that any and all steps are being taken in response. We would like to thank all parties for their cooperation and patience during this period,” the spokesperson said.
“We are working to verify these claims by the unauthorised party as a priority and will provide further details as and when we have more information. If we detect that information has been accessed, we will contact affected parties as required to provide support and guidance in how to respond.”
Followmont also asked “interested parties” not to seek to access the threat actor’s leak seat, as that only promotes further crime and may even be a risk to personal security.
“Followmont takes cyber security seriously, and we are committed to keeping our stakeholders updated as we work to respond,” the company’s spokesperson said.
“We would like to thank them for their support and understanding while our investigation is underway.”
Akira has been relatively inactive recently, with its attack on Followmont Transport its first since 4 October, when it listed two victims: the US-based Tanya and Riley Gear Corporation. All up, it claimed 11 victims that month.
Like many gangs, Akira traced its history back to the infamous Conti ransomware operation, which fell apart in 2022 due to internal divisions regarding Russia’s invasion of Ukraine. Akira was first observed in operation in March 2023 and is a ransomware-as-a-service operation.
According to reports from victims, Akira’s ransoms typically range from US$200,000 to more than US$4 million. Akira’s last major Australian victim was Panasonic Australia, which fell victim to the gang back in June.
Followmont Transport operates a fleet of more than 1,000 vehicles serving customers in Queensland and NSW and has almost 1,000 employees. According to its website, the company has more than 20,000 customers, including Australia Post, Mitre 10, Dulux, and Repco.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.