Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
The gang behind GoAnywhere and MOVEit hacking campaigns is at it again with the latest file transfer vulnerability.
After news broke last week of a series of vulnerabilities in Cleo’s managed file transfer applications and that they were being actively exploited, the Clop ransomware gang has admitted it is the threat actor behind the campaign.
A Clop spokesperson told Bleeping Computer last week it was responsible for a campaign already observed by researchers at cyber security firms Huntress and Rapid7.
“As for CLEO, it was our project (including the previous Cleo) – which was successfully completed,” the spokesperson said after Bleeping Computer reached out.
“All the information that we store, when working with it, we observe all security measures. If the data is government services, institutions, medicine, then we will immediately delete this data without hesitation (let me remind you about the last time when it was with MOVEit – all government data, medicine, clinics, data of scientific research at the state level were deleted), we comply with our regulations.”
The ransomware gang has also said, on its darknet leak site, that it will shortly be removing data from past attacks to make way for the newly stolen data from this campaign, suggesting another widespread series of data breaches.
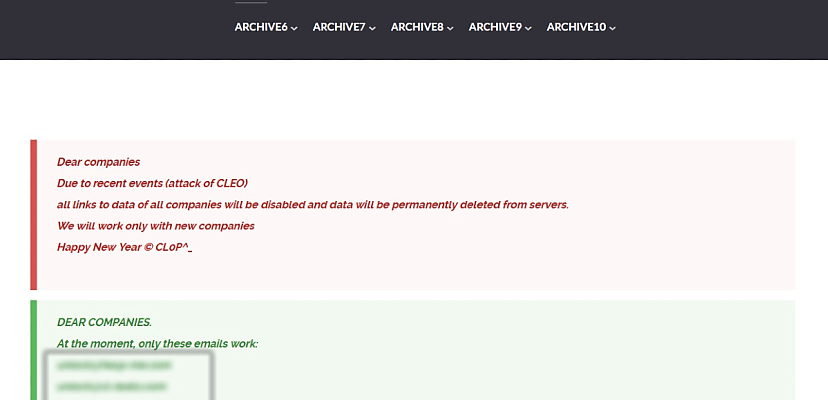
“Due to recent events (attack of CLEO),” the gang said, “all links to data of all companies will be disabled and data will be permanently deleted from servers”.
“We will work only with new companies.”
Researchers have been tracking active exploitation of vulnerabilities in Cleo VLTrader, Cleo Harmony, and Cleo LexiCom – which were all patched in October when Cleo released version 5.8.0.21 of all three solutions – since at least 9 December. The programs were all supposedly patched; however, the vulnerability remained.
Rapid7 was tracking multiple instances of successful exploitation as of last week.
“As of December 10, Rapid7 MDR has confirmed successful exploitation of this issue in customer environments; similar to Huntress, our team has observed enumeration and post-exploitation activity and is investigating multiple incidents,” Rapid7 said in an 11 December update to its blog post on the activity.
Clop has experience with this type of campaign. Last year, it was responsible for widespread data breaches after exploiting similar vulnerabilities in the GoAnywhere and MOVEit file transfer applications, which exposed the data of thousands of companies. The gang has not yet started publishing data from this campaign.
According to its website, Cleo has around 4,200 customers. However, Rapid7’s head of vulnerability research, Caitlin Condon, said there is only a small population of exposed systems.
“A naive query to an internet exposure engine shows a relatively small population of internet-exposed systems (i.e., in the mid- to high hundreds, depending on the query). Any affected system on the open internet is easy to find and exploit if a threat group already has a working exploit,” Condon said.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.