Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Full configuration files have been shared on a hacking forum, including IP addresses and passwords, all for free, suggesting a “very serious cyber incident” is about to go down.
A new hacking group has just become a part of the ongoing saga regarding a recently disclosed critical vulnerability in Fortinet FortiGate firewall devices.
Essentially, the keys to more than 15,000 vulnerable devices were shared on a popular hacking forum overnight, and the data looks not only legitimate but very dangerous.
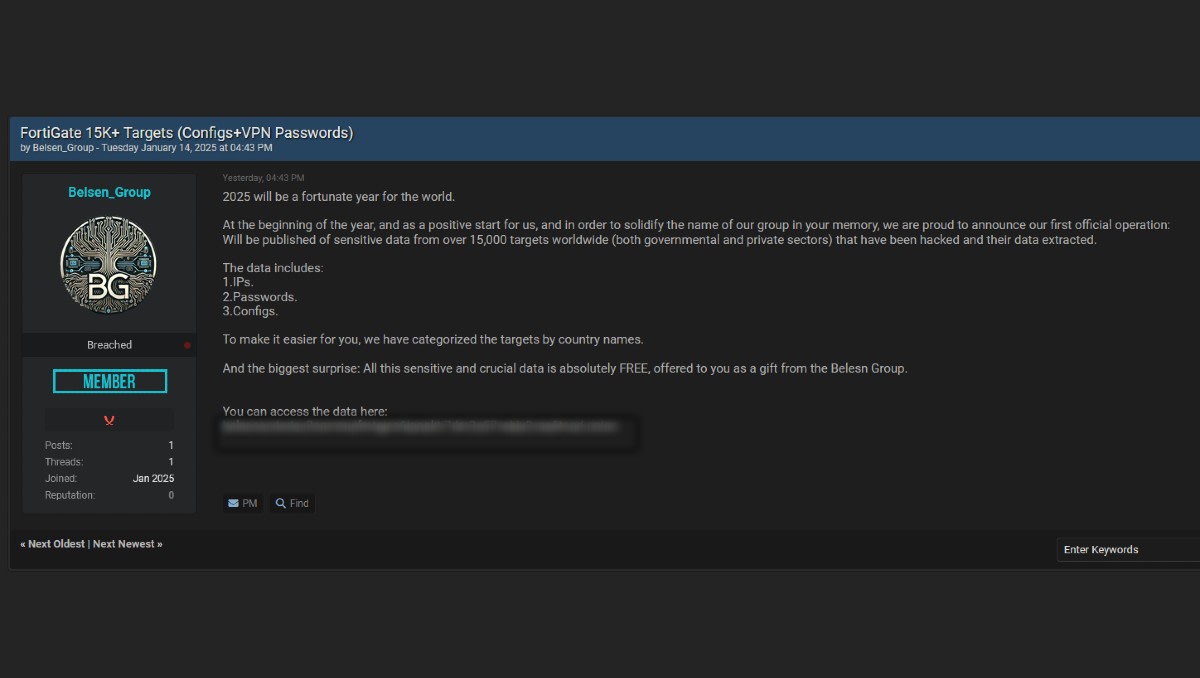
The Belsen Group – which only joined the forum on 3 January – boasted in its 14 January post that “2025 will be a fortunate year for the world”.
“At the beginning of the year, and as a positive start for us, and in order to solidify the name of our group in your memory, we are proud to announce our first official operation,” the Belsen Group said.
“Will be published of sensitive data from over 15,000 targets worldwide (both governmental and private sectors) that have been hacked and their data extracted.”
The data, 1.6 gigabytes of it in a .ZIP archive, is being hosted on the group’s darknet site and appears to include IP addresses, passwords, and full configuration data.
“And the biggest surprise: All this sensitive and crucial data is absolutely FREE, offered to you as a gift from the Belesn [sic] Group,” the group said.
According to cyber security specialist Kevin Beaumont, the data is the real deal.
“The ZIP contains a folder for each IP address, inside is config.conf (Fortigate full config dump) and vpn-passwords.txt,” Beaumont said in a post on Mastodon.
“The FortiGate config data appears legit – they’re unique – and it looks like a very serious cyber incident is going to play out. Some align to Shodan.
“All the configs appear to come from Fortigate 7.x devices, so this is probably the latest zero-day Fortinet didn’t tell people about.”
Beaumont also confirmed one of the username and password combinations and added that Fortinet’s recently released CVE (see below) may not cover the entire scope of the issue.
“A small number of the devices are on Fortigate 7.2, versions from late 2022 – which tends to blow the recent CVE out of the water as that’s not supposed to be impacted,” Beaumont said in a follow-up post.
In a later blog post, however, Beaumont observed following further investigation that the files relate to and earlier CVE, disclosed by Fortinet in 2022, CVE-2022–40684.
"I’ve done incident response on one device at a victim org, and exploitation was indeed via CVE-2022–40684 based on artefacts on the device. I’ve also been able to verify the usernames and password seen in the dump matches the details on the device," Beaumont said.
"The data appears to have been assembled in October 2022, as a zero-day vuln. For some reason, it has been released today, just over 2 years later."
Beaumont added "Even if you patched back in 2022, you may still have been exploited as the configs were dumped years ago and only just released — you probably want to find out when you patched this vuln".
The Belsen group is likely releasing this dump now to take advantage of news of Foritgate's most recently disclosed vulnerability.
Fortinet recently addressed Arctic Wolf’s 10 January revelation that its Fortinet FortiGate firewall devices had been impacted by a widespread hacking campaign late last year, when it officially disclosed CVE-2024-55591 and released its own mitigation advice this week.
“An Authentication Bypass Using an Alternate Path or Channel vulnerability [CWE-288] affecting FortiOS and FortiProxy may allow a remote attacker to gain super-admin privileges via crafted requests to Node.js websocket module,” FortiGuard Labs said in Product Security Incident Response Team update dated 14 January.
“Please note that reports show this is being exploited in the wild.”
It appears that the exploitation may just be beginning. As Fortinet said, it’s time to make sure your FortiGuard appliances are fully up to date; in addition, HTTP/HTTPS access to the administrative interface should either be disabled or have the IP addresses that can access it limited.
UPDATED 16/01/25 to add further information from Kevin Beaumont.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.