Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Threat actors confuse two similarly named companies in a case of mistaken identity that proves even hackers – and analysts – can make mistakes.
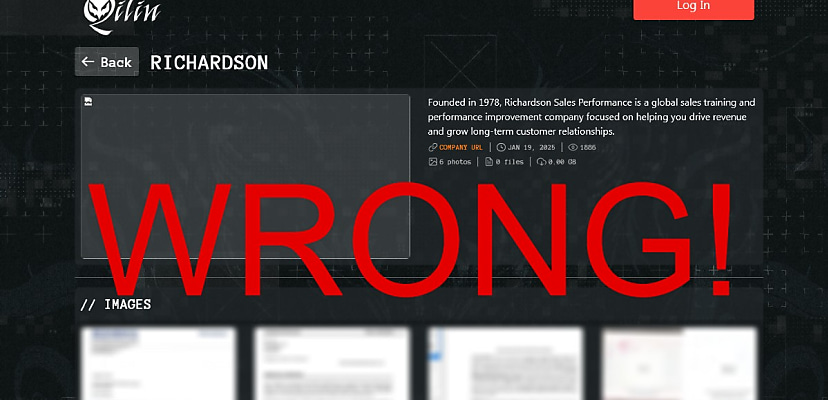
On 19 January, the Qilin ransomware gang listed sales and management consultant firm Richardson Sales Performance as a victim on its darknet leak site.
The company was mentioned by name, its URL was included in the leak post, and even a boilerplate description of the Richardson Sales Performance was lifted from various directory sites, such as Zoominfo and Datanyze.
Subsequently, the company was listed on numerous threat intelligence feeds, including VenariX’s Telegram feed and Ransomware.live, as the victim of a ransomware attack.
There was only one little problem: Richardson Sales Performance was not the victim.
“Richardson Sales Performance, www.Richardson.com, is aware of a small number of media reports indicating that it is suffering a ransomware attack,” a Richardson spokesperson told Cyber Daily.
“We would like to assure our clients that such reports about Richardson Sales Performance are mistaken. We have not suffered a ransomware attack or other cyber security incident. We remain fully operational and eager to serve our clients.”
Cyber Daily initially reached out to the company, which is headquartered in the United States, as Richardson has offices around the world, including in Australia. Plus, it has a wide range of well-recognised brands as clients, such as Cisco, Maersk, American Express, and Ericsson. A breach of a company of that scale could be quite impactful – assuming it actually happened.
However, what actually happened is that the ransomware operators compromised a company called Richardson Projects, which is based in Sri Lanka. Even the evidence shared by Qilin points directly to Richardson Projects, including correspondence with the Sri Lankan company’s letterhead, personal information including addresses in Sri Lanka, and several scans of passports belonging to Sri Lankan nationals employed by Richardson Projects, including some of its senior executives.
It is, basically, a case of mistaken identity. That said, how a group of hackers could actively target an organisation in one country and mistake it for another in a different country entirely – despite actually having the evidence in their hands – is a bit beyond comprehension. Just because hackers are often technically capable does not necessarily make them clever, it would appear.
To be sure, this could be a significant incident for Richardson Projects, but at the moment, it’s an incident that has effectively slipped under the radar because of the hackers’ error, compounded by the fact that many threat intelligence feeds automate their tracking of ransomware operators and take the threat actors’ claims at face value.
This, in turn, has led to a company that has not been involved in any kind of data breach being listed as a ransomware victim on numerous websites and even entire news articles written about the alleged incident
Automated tracking of darknet leak sites is all well and good, and Cyber Daily makes extensive use of such services – but a human in the loop is still essential if you want to actually get to the truth.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.