Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Clop listed dozens of victims on its darknet leak site in the last 24 hours, all allegedly part of last year’s mass exploitation of Cleo’s managed file transfer software products.
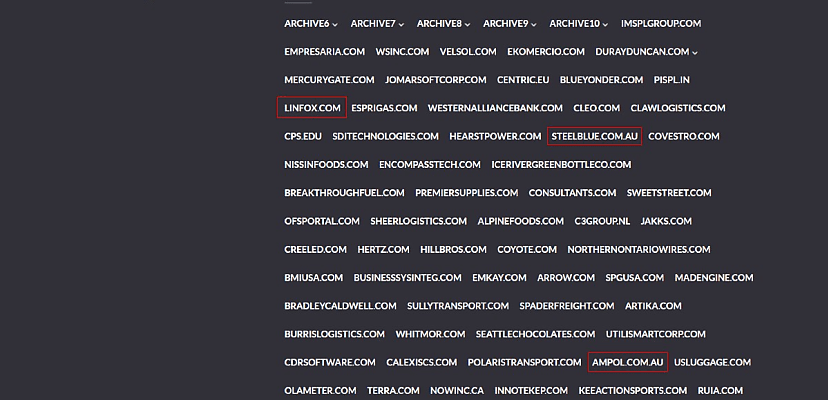
Late last year, the Clop ransomware gang declared that it had actively exploited vulnerabilities in a raft of file transfer products developed by software company Cleo. Now, overnight, the gang has listed 60 alleged new victims linked to that exploitation on its darknet leak site.
Included in the mass listing are three well-known Australian companies: transport energy provider Ampol, logistics firm Linfox, and shoe-maker Steel Blue.
“We have data of many companies who use Cleo. Our teams are reaching and calling your company and provide your special secret chat,” a gang spokesperson said in a 23 January post.
“If you are not sure if we have your data,” Clop added, “email us”.
“You have until Friday if all the data is published after that.”
Of the 60 victims listed – which includes Cleo itself and Blue Yonder, which was also part of a broader supply chain attack last year – six have already had their data published online.
The gang also hinted at another 50 companies yet to be named, with Clop only sharing the first two letters of each.
“This is the next list which we have closed for the time being and do not show the names in full,” Clop said.
“If you do not get in touch asap the list will be open.”
A spokesperson for Clop told Bleeping Computer in December 2024 that it was the threat actor behind the widespread exploitation of three Cleo products: Cleo VLTrader, Cleo Harmony, and Cleo LexiCom.
“As for CLEO, it was our project (including the previous Cleo) – which was successfully completed,” the spokesperson said.
At the time, the gang removed all data published via previous attacks, saying instead it was now going to focus on extorting its new set of Cleo victims. Cyber security firms Rapid7 and Huntress were both tracking and investigating multiple incidents of exploitation as of early December. While Cleo has more than 4,000 customers, Rapid7’s head of vulnerability research, Caitlin Condon, believed that only a small percentage of Cleo customers were actively compromised.
“A naive query to an internet exposure engine shows a relatively small population of internet-exposed systems (i.e., in the mid- to high hundreds, depending on the query). Any affected system on the open internet is easy to find and exploit if a threat group already has a working exploit,” Condon said.
Cyber Daily has reached out to Ampol, Linfox, and Steel Blue for confirmation of Clop’s claims.
File transfer exploits are one of Clop’s specialties. The gang was also responsible for mass compromises of MOVEit and GoAnywhere file transfer customers throughout 2023 and 2024. The gang is thought to be based in Russia.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.