Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Threat feed and intelligence data SaaS platform FalconFeeds.io announced that threat actors took control of its X (formerly Twitter) account to promote a cryptocurrency scam.
FalconFeeds is a tool for cyber security professionals, businesses and more that allows users to monitor threats and cyber security incidents, identify and analyse threat actors and map out threat campaigns.
On 25 January, the company announced that just days prior, threat actors compromised its X account, bypassing multifactor authentication (MFA) and spammed promotions for a crypto scam.
“On 23rd January 2024, 6 PM PST, our Twitter account was compromised by crypto scammers, even with MFA enabled,” said FalconFeeds on X.
“Unfortunately, we lost access and witnessed one of the largest scamming incidents we’ve ever experienced. The scammers managed to post nearly one tweet every minute, resulting in over 60+ fraudulent tweets every hour till 1:30 am PST on 24th January.
“This incident comes after months of persistent, multi-vector attacks targeting us for exposing threat actors and their false claims. As challenging as this has been, we remain steadfast in our mission to shine a light on malicious activities.”
If you're going to compromise a Twitter account to push your cryptocurrency drainer — you DON'T need to spam it every 45 seconds.
— vx-underground (@vxunderground) January 24, 2025
Holy Christ, we get it, you're trying to drain crypto-wallets. Could you make it ANY more obvious? pic.twitter.com/TkISZklHjS
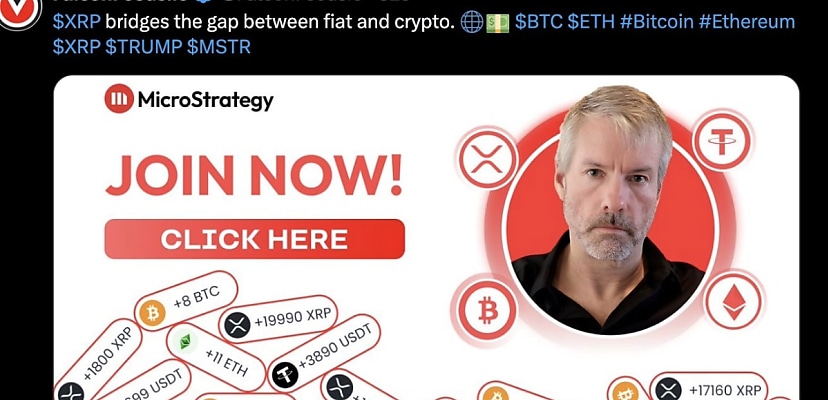
While the scam posts have since been removed, the posts made claims about popular crypto such as bitcoin, XRP, Ethereum, $TRUMP, and more. The link within the posts took users to a fake giveaway page from a company called MicroStrategy, a business intelligence company that works heavily with bitcoin and cryptocurrency.
FalconFeeds said that through direct work with X, it regained access to the account.
“We sincerely apologise for the alarming content posted during this period and the inconvenience caused to our followers. Rest assured, a detailed release on the incident, including a thorough analysis of the scammer group, will be coming soon,” it said.
The company also thanked the cyber security community for its support, identifying the breach, spreading awareness, and assisting in the recovery process.
“While this event has been embarrassing, it strengthens our resolve to continue exposing threat actors. Thank you for standing with us during this time. Stay tuned for our detailed blog and release in the coming days,” it said.
At this stage, the threat actor behind the incident has not been publicly named. Cyber Daily has reached out to MicroStrategy for comment on the incident.

Be the first to hear the latest developments in the cyber industry.