Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
According to Dragos’ latest industrial ransomware analysis, ransomware gangs caused widespread disruptions of critical infrastructure during the last quarter of 2024.
Dragos has released its Industrial Ransomware Analysis report for the fourth quarter of 2024, and it makes for a pretty grim reading.
Established ransomware operators were expanding their reach, while several new or rebranded groups appeared on the scene, with a focus on targeting industrial environments. Several others were observed taking advantage of legitimate cloud services as part of their attack chain.
According to Dragos, this may signal a shift to cloud-centric tactics, making incident detection and response even more of a challenge.
Ransomware groups and tactics
Ransomware operators to watch are BianLian and RansomHub, which have formed an alliance of sorts, with the latter sharing advanced tools to exploit remote desktop services and VPN devices.
Meanwhile, DragonForce is working with affiliates with experience in specialised intrusion techniques as it focuses its attacks on entities in the transportation and manufacturing industries.
On the other hand, the Interlock group was observed targeting FreeBSD machines in critical infrastructure settings, which Dragos notes is part of a “broader trend of adversaries bypassing standard Windows defences to disrupt essential services”.
Termite is another gang making waves and has been seen actively targeting supply-chain entities. The gang uses advanced encryption techniques and “aggressive process termination capabilities”, which Dragos believes could pose a threat to downstream oil and gas industries and manufacturing.
While many ransomware groups continue to rely upon living-off-the-land techniques to establish persistence and deploy code, several operators have turned to cloud-centric extortion tactics, using Azure Storage Explorer and AWS S3 Transfer Acceleration to exfiltrate data before encryption.
“Although Dragos has not observed any OT-focused compromise resulting directly from these cloud-centric intrusion methods, adversaries who gain a foothold through such tactics can potentially escalate their attacks, impacting OT environments or critical IT systems that support industrial operations,” Dragos said.
Who was hacked, where, and by who
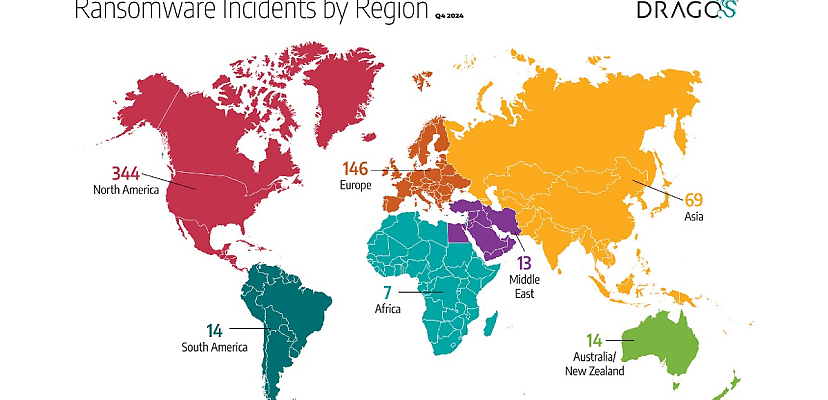
North America remained the most targeted region, with 344 ransomware incidents for the quarter (mostly in the United States), followed by Europe with 146 and Asia with 69. Fourteen Australian and New Zealand organisations were targeted, the same number of incidents that occurred across South America. Thirteen incidents were tracked in the Middle East and seven in Africa.
The most impacted sector was manufacturing, which bore the brunt of 70 per cent of all attacks, with the construction sub-sector getting hit particularly hard, with 117 incidents out of a total of 424 for the quarter.
Transportation was the next most targeted, with 69 ransomware incidents, followed by industrial control systems, with 58.
Despite law enforcement takedowns and arrests, LockBit remained the most active ransomware group, with 70 incidents, followed by Play with 63 and RansomHub with 56. The three groups alone accounted for roughly 31 per cent of all ransomware activity in the fourth quarter.
Three attacks in particular were notable for the disruption and damage caused. Costa Rica’s state-owned energy provider was forced into manual operation after its digital systems were taken offline following a ransomware attack, while an attack on Pittsburgh Regional Transit in the US caused public transport delays lasting hours.
However, an attack on beverage giant the Stoli Group was particularly impactful, with several of its US subsidiaries filing for bankruptcy following extensive IT outages.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.