Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
The hackers claim to have stolen 81 gigabytes of data, including information related to human resources at the NSW-headquartered firm.
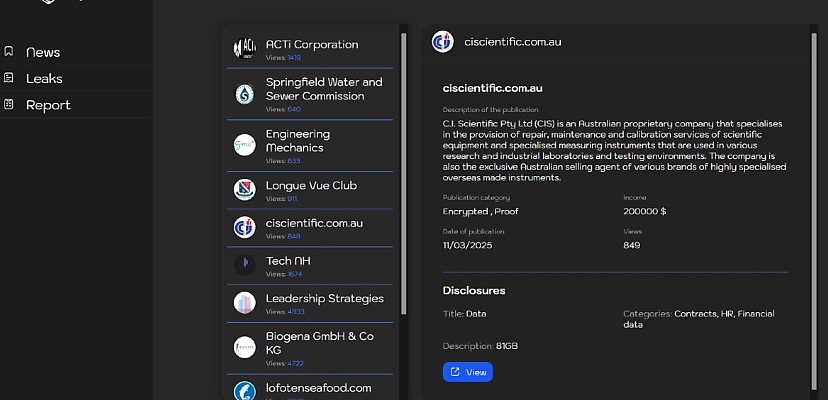
The Lynx ransomware gang has listed CI Scientific – currently rebranding as CISCAL – as a victim on its darknet leak site.
In a leak post dated 11 March, the hackers claimed to have stolen 81 gigabytes of data, which allegedly includes business contracts, financial data, and human resources information.
No evidence has been published (though there is a link to a currently empty directory that looks as though it should be displaying some form of file directory), nor has Lynx listed a ransom amount or deadline.
Curiously, the website that Lynx listed as belonging to CI Scientific as ciscientific.com.au is an address that no longer appears to exist. CI Scientific’s current site is ciscal.com.au, suggesting the hackers may have accessed a legacy server belonging to the company.
CI Scientific is an Australian supplier of laboratory and industrial equipment and is a leading supplier to organisations in New Zealand and the Pacific region. The company also offers calibration services for scientific and industrial equipment.
CI Scientific is headquartered in Seven Hills, NSW, and has offices in Queensland, Victoria, and the Philippines.
Cyber Daily reached out to CI Scientific for comment on the hackers’ claims but has yet to receive a response.
The Lynx ransomware operation was first observed in July 2024 and has since then claimed 193 victims, including CI Scientific. The gang’s most recent Australian victim was truck dealership Brown and Hurley, which Lynx claimed to have hacked in February. CI Scientific is the gang’s fourth Australian victim in 2025
In a “press release” published in the gang’s leak site in July 2024, Lynx said its “clear intention” is to avoid “undue harm” to the companies it targets.
“We recognise the importance of ethical considerations in the pursuit of financial gain and maintain a strict policy against targeting governmental institutions, hospitals, or non-profit organisations, as these sectors play vital roles in society,” Lynx said.
“Our operational model encourages dialogue and resolution rather than chaos and destruction. We believe that fostering an environment where businesses can engage in constructive problem-solving can lead to better outcomes for all parties involved.”

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.