Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Security researchers say that a recent post on a hacking forum claiming a massive breach of Oracle Cloud appears legitimate.
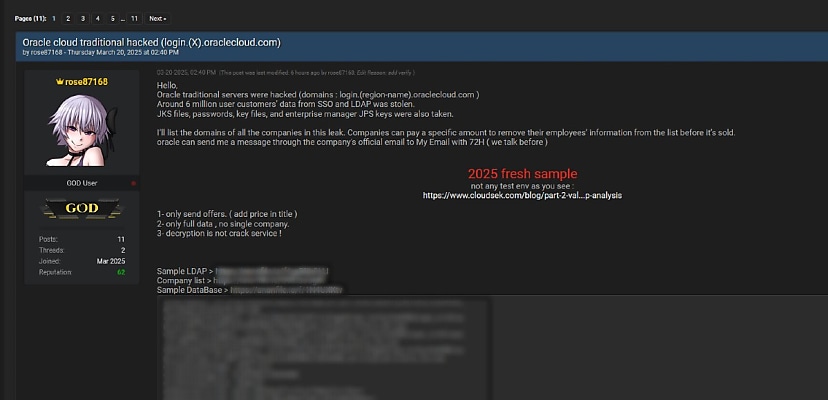
A member of a popular hacking forum made an alarming claim last week – they had successfully breached Oracle Cloud infrastructure and stolen the credentials of approximately six million customers.
According to a list of more than 140,000 organisations impacted by the alleged breach, several Australian companies have been affected, including Optus, Woolworths, and Nine Entertainment. Government agencies were also included in the list of compromised victims, including the Australian Taxation Office and the Defence Department.
In the wake of the claim, potentially impacted organisations scrambled to update their Oracle credentials, despite Oracle itself denying any breach occurred.
“The published credentials are not for the Oracle Cloud,” an Oracle spokesperson said.
“No Oracle Cloud customers experienced a breach or lost any data.”
However, researchers at cyber security firm CloudSEK believe otherwise and have said the hacker’s claims are entirely correct.
Using a combination of CloudSEK’s own Nexus platform and human intelligence, the company confirmed that one login endpoint the hacker said they accessed – login.us2.oraclecloud.com – is a legitimate production SSO environment and that the domains listed by the hacker matched up to domains in Oracle partner guides and public GitHub repositories.
“We’re driven by transparency and evidence, not speculation,” Rahul Sasi, CEO and Co-founder of CloudSEK, said in a statement.
“This follow-up report equips the community and Oracle with facts to investigate and mitigate this threat responsibly.”
According to CloudSEK, the breach could have several long-term implications, including ongoing risks of cyber espionage and further unauthorised access of Oracle customers, extortion, and supply chain disruption.
The hacker has been updating their original post, including details of CloudSEK’s investigations, and adding further sample datasets, and initially gave companies a chance to pay to have their data removed.
“I’ll list the domains of all the companies in this leak. Companies can pay a specific amount to remove their employees’ information from the list before it’s sold,” the hacker – using the handle rose87168 – said.
The hacker also claimed to have been in contact with Oracle previously and that the company had their contact information.
“Oracle can send me a message through the company’s official email to My Email with 72H (we talk before ),” the hacker said.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.