Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Analysis by Kaspersky’s Global Emergency Response team has found that hacking passwords and exploiting software vulnerabilities were the most common cyber attack methods used last year.

The new Incident Response Analytics Report has revealed that brute force (when hackers guess login info through trial-and-error) accounted for 31.6 per cent of cyber attacks on businesses last year. This share has skyrocketed from 13 per cent in 2019 – likely spurred by the move to remote working.
Vulnerability exploitation (31.5 per cent) was the other common method used to infiltrate a company’s network – when attackers take advantage of an error in the code or logic of an operating system or application software.
Malicious emails accounted for 23.7 per cent of initial access vectors during attacks.
According to Kaspersky's analysis of anonymised data from incident response cases, the attackers only exploited vulnerabilities from 2020 in a few incidents. In other cases it was older, unpatched vulnerabilities such as CVE-2019-11510, CVE-2018-8453, and CVE-2017-0144.
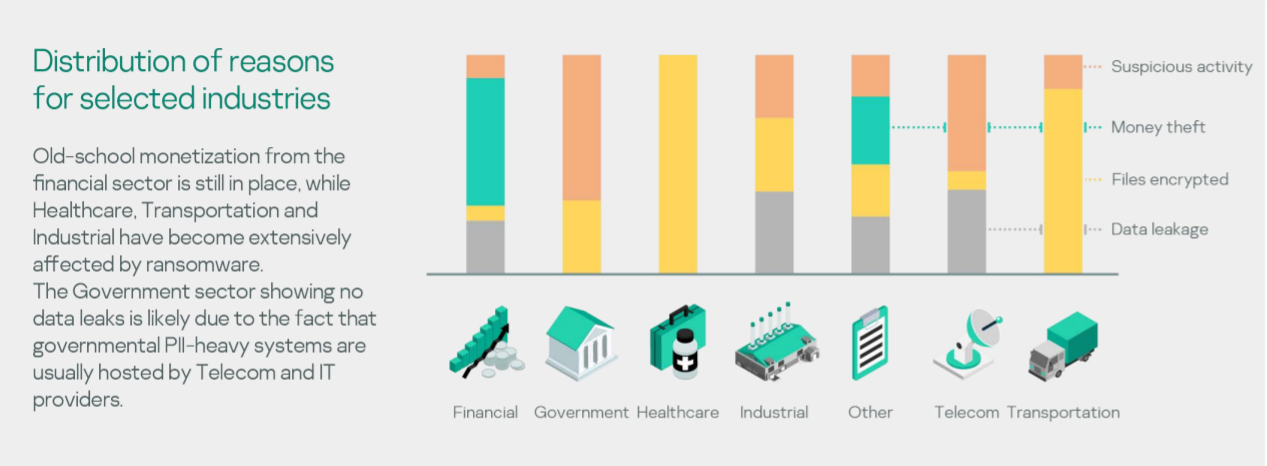
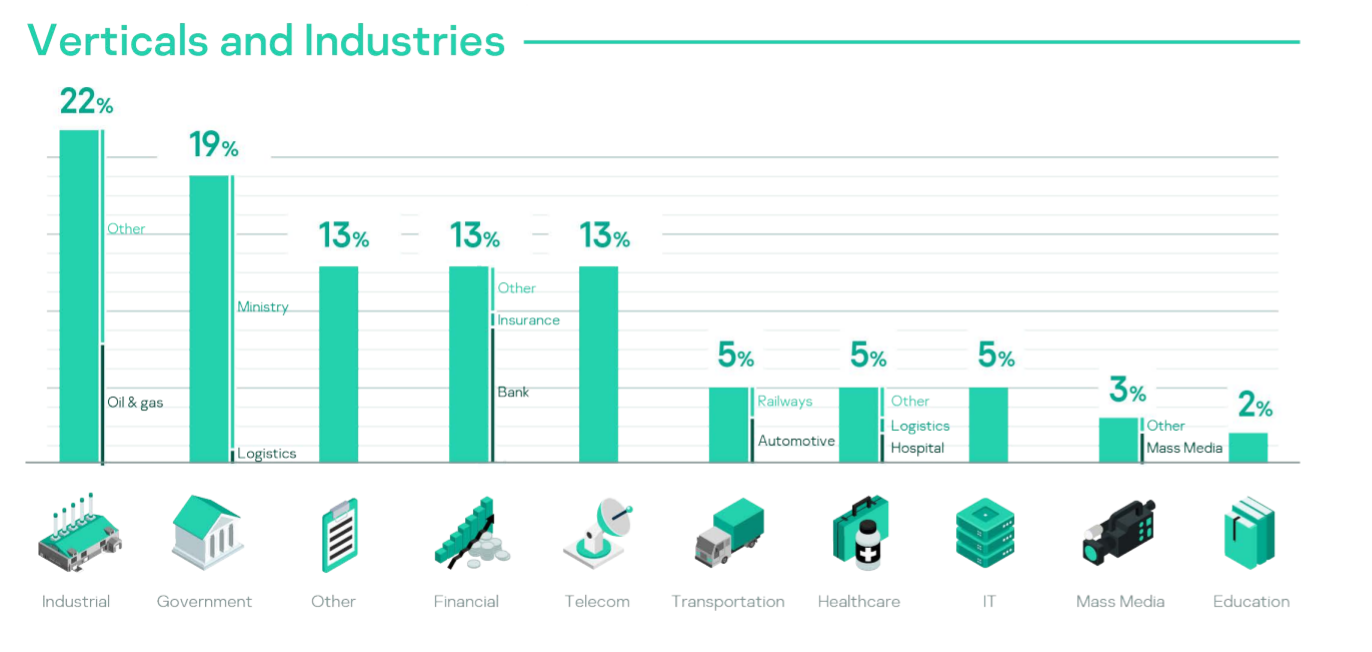
Source: Kaspersky
According to Konstantin Sapronov, head of Kaspersky’s global emergency response team, this demonstrates how simply having a robust password policy in place and applying available patches to software can reduce the likelihood of being a victim of a cyber attack by 60 per cent.
“Even if the IT teams do its best to secure the company’s infrastructure, factors such as legacy systems, low-end equipment, compatibility issues and human factors can often result in security breaches that can jeopardise an organisation’s security,” Sapronov said.
“Protective measures alone can’t provide holistic cyber defence.
"Arming themselves with detection and response tools that can recognise and eliminate an attack at an early stage, as well as address the cause of the incident can help businesses reduce the cost of such an attack.”
The research also shows over half of all attacks that started with malicious emails, brute force or exploitation were detected within hours (18 per cent) or days (55 per cent).
While prevention of brute force attacks and the control of timely updates are not problematic for professional cyber security teams, in practice it’s virtually impossible to 100 per cent eliminate these issues using these methods alone.
Businesses can follow a few simple steps to minimise their chances of being compromised by such an attack, to ensure that patch management or compensation measures for public-facing applications have zero tolerance Sapronov added.
“Implement a robust password policy across the business, including multifactor authentication and identity and access management tools,” Sapronov said.
"Regular updates of vulnerability details from software vendors, scanning the network for vulnerabilities and patch installations are crucial for the security of a company’s infrastructure.
“And lastly, train your employees in security awareness, and be sure to conduct training on an ongoing basis to maintain a high level of awareness among your team.”
The full Incident Response Analytics Report is available on Securelist with further detail and advice on how to protect businesses against such attacks.

Nastasha is a Journalist at Momentum Media, she reports extensively across veterans affairs, cyber security and geopolitics in the Indo-Pacific. She is a co-author of a book titled The Stories Women Journalists Tell, published by Penguin Random House. Previously, she was a Content Producer at Verizon Media, a Digital Producer for Yahoo! and Channel 7, a Digital Journalist at Sky News Australia, as well as a Website Manager and Digital Producer at SBS Australia. Nastasha started her career in media as a Video Producer and Digital News Presenter at News Corp Australia.
Be the first to hear the latest developments in the cyber industry.