Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Emotet, once considered one of the most dangerous forms of malware, is back just months after an extensive international operation disabled its infrastructure in January earlier this year, according to G DATA.

G DATA has reported it observed activity on several of their TrickBot trackers that the bot tried to download a DLL to the system on Sunday, 14 November, at around 9:26pm UTC. According to G DATA's internal processing, these DLLs have been identified as Emotet.
Since the botnet was taken down earlier this year, G DATA was suspicious about the findings and conducted an initial manual verification. Following initial results and IOCs, G DATA has "high confidence" that the samples could be a reincarnation of the infamous Emotet.
Initial G DATA analysis
The first occurrence of the URLs being dropped was recorded by G DATA on Sunday, 14 November, 9:26pm.
The URL received was hxxp://141.94.176.124/Loader_90563_1.dll (SHA256 of the drop: c7574aac7583a5bdc446f813b8e347a768a9f4af858404371eae82ad2d136a01).
Internal processing detected Emotet when executing the sample in the G DATA sandbox systems. Notably, the sample seems to have been compiled just before the deployment via several TrickBot botnets was observed: Timestamp: 6191769A (Sun Nov 14 20:50:34 2021).
The network traffic originating from the sample closely resembles what has been observed previously (e.g., as described by Kaspersky): the URL contains a random resource path, and the bot transfers the request payload in a cookie.

Additionally, the sample now uses HTTPS with a self-signed server certificate to secure the network traffic. However, the encryption used to hide the data seems to be different from what has been observed in the past.
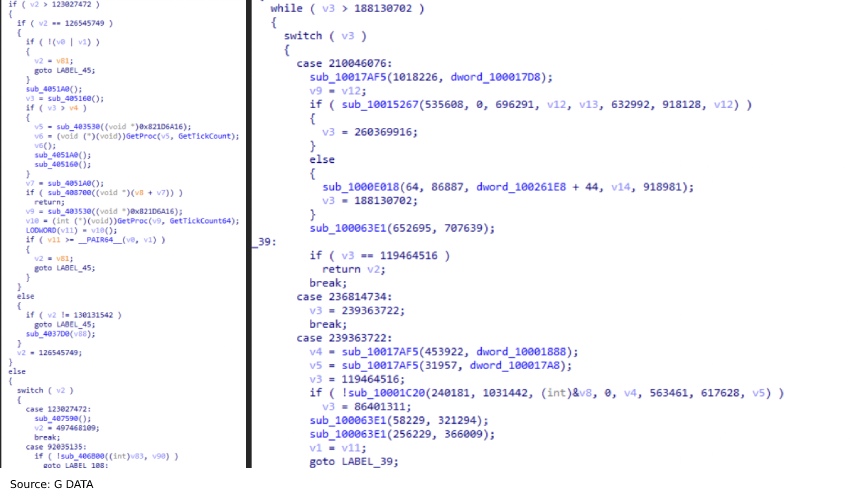
A notable characteristic of the previous Emotet samples was the heavy use of control-flow flattening to obfuscate the code.
The current G DATA sample also contains flattened control flows, and to illustrate the similarity in the style of the obfuscation. For comparison, G DATA has provided two arbitrary code snippets – the left side is a sample from 2020, on the right is a snippet from the recent 2021 sample.
In light of the Emotet resurgence reports, Proofpoint have also confirmed overnight that it has detected new email delivery of Emotet in its data.
According to Sherrod DeGrippo, vice-president, threat research and detection at Proofpoint, the threat actor could be rescaling operations.
“Proofpoint Threat Research observed the return of Emotet delivering messages to government, non-profit and commercial organisations predominantly in the United States and Canada.
"The top five verticals included financial services, insurance, transportation, technology and manufacturing.
"These do not appear to be tests. They are active campaigns," DeGrippo said.
One of the key differences between the new sample of Emotet observed and previous samples is the reduced scale, with Proofpoint reporting it has not seen the same larger volumes (above 50,000 messages) that had previously been observed prior to the international law enforcement actions in January 2021.
The current sample is showing new items including the integration of XLS and XLM files for delivery that if a user enables macros, Emotet is installed.
The actor also replaced the RSA encryption of APIs with ECC (elliptic-curve cryptography). Proofpoint reports that it continues to see thread hijacking, similar attachment names and the use of Word documents and password-protected ZIP files in delivery as previously observed. A number of the files’ names look legitimate. The payload URLs are still distributed in sets of seven, along with the same botnet ID generation, to name a few.
Based on some of the infrastructure Proofpoint observed in campaigns, the actors are leveraging bulletproof hosting providers to rescale operations.
CrowdStrike Intelligence weighs in on the return of Emotet, observing that Emotet's TrickBot delivery resurgence can be associated with the malware and the e-crime adversary group WIZARD SPIDER.
The dismantling of the Emotet network by Europol in January 2021 only had a temporary effect as suspected, according to Adam Meyers, SVP of intelligence, CrowdStrike.
"WIZARD SPIDER is a sophisticated eCrime group whose arsenal also includes malware such as Ryuk, Conti and Cobalt Strike.
The takeover of Emotet by WIZARD SPIDER impressively shows how resilient the eCrime milieu has become by now," Meyers concluded.
Emotet has consistently been one of the largest volume threats on the internet for years and its return represents a significant threat to organisations' security posture.
[Related: FBI external emails hacked; hackers send out bogus messages]

Nastasha is a Journalist at Momentum Media, she reports extensively across veterans affairs, cyber security and geopolitics in the Indo-Pacific. She is a co-author of a book titled The Stories Women Journalists Tell, published by Penguin Random House. Previously, she was a Content Producer at Verizon Media, a Digital Producer for Yahoo! and Channel 7, a Digital Journalist at Sky News Australia, as well as a Website Manager and Digital Producer at SBS Australia. Nastasha started her career in media as a Video Producer and Digital News Presenter at News Corp Australia.
Be the first to hear the latest developments in the cyber industry.