Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
NSW Police posted a warning on their official Facebook page about the new FluBot phishing texts that have been making the rounds, sending malware links that enable download and installation of malicious software on to devices.

According to Scamwatch, many Australians have been receiving scam text messages about missed calls, voicemails, deliveries and photo uploads since August 2021.
The text messages ask recipients to tap on a link to download or access something. Doing so will download a specific type of malware to your device. These are “FluBot” text messages.
Scamwatch is run by the Australian Competition and Consumer Commission (ACCC), and it provides information to consumers and small businesses about how to recognise, avoid and report scams.
What is FluBot?
FluBot is malicious software (malware) that sends text messages to both Androids and iPhones.
There are a large number of different types of FluBot text messages and scammers are updating these all the time. Scamwatch strongly recommends to never click on the links in these messages. It is best to delete these immediately.
Android phones are more at risk. The content of the text messages varies but these all contain a link containing five to nine random numbers. These will often ask you to download an app to track or organise a time for a delivery, hear a voicemail message, or view photos that have been uploaded.
It is important to note that there is no delivery, voicemail, or photos uploaded and the app is actually malware called FluBot.
If you have an Android device, typically the application downloaded is called Voicemail71.apk, Update42.apk’ or DHL34.apk. This application is malware.
The application may be able to:
Installing the software is likely to give scammers access to your passwords and accounts. They may be able to use this information to steal your money or personal information.
It will also ask other infected Australian phones to send FluBot messages to the numbers it steals from your phone, continuing and expanding the scam.
So, if a user called the person that sent you the message, it would be another victim of the scam whose device was infected.
Apple devices cannot be infected with FluBot but will likely be infected with other malware if you click on these links.
How does FluBot work?
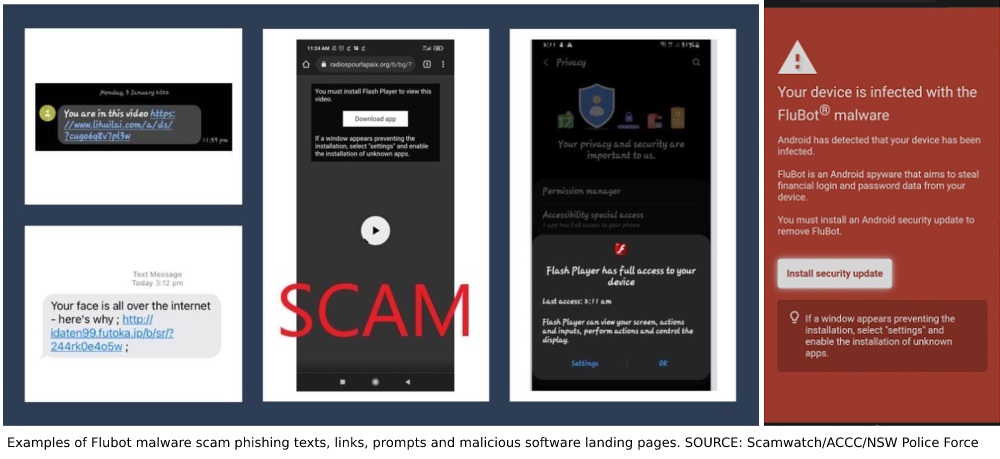
FluBot text messages are sent with a link which almost always contains a series of five to nine random letters and numbers at the end. Here's a list of what typically occurs:
If a user clicks or taps on the link, it will usually go to a screen where you will be asked to download an app for a purpose that relates to the text message.
For example, if the text message was about a delivery, the screen will likely show courier branding and a button or link which directs to downloading an app to track the progress of the “delivery”.
Clicking the link may lead to a page which states that a device has already been infected with FluBot and that “security updates” need to be installed to remove it.
This is a tactic by the scammers, designed to scare users into clicking the “install” button. Clicking this infects your device with the FluBot malware. These pages will often say that a window may appear preventing the installation, and that you should enable the installation via your device's settings. This is another trick to move you through the process and download the malware to your device.
How to avoid your device from being infected
Have you downloaded the FluBot malware?
Act immediately. If you’ve already clicked the link to download the application, your passwords are at risk from hackers.
Cleaning your device
Remove the malicious software from your Android device using these steps:
Learn more about FluBot scams and other relevant phone scams on the Scamwatch website.
[Related: Akamai’s latest report reveals the persistence of online piracy]
Be the first to hear the latest developments in the cyber industry.