Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Most ransomware attacks appear to be financially motivated, but new Chainalysis research found that others appear to be motivated by geopolitical goals, and seem more geared toward deception, espionage, reputational damage and disruption of the enemy government’s operations.

In cases where a ransomware strain contains no mechanism to collect payment or allow victims to recover their files, Chainalysis researchers are more certain that money isn't the attackers' primary motivation as they have found in a recent ransomware attack on Ukrainian government agencies by hackers believed to be associated with the Russian government.
As the Computer Emergency Response Team of Ukraine (CERT-UA) described, the attack occurred on the night of 13 January 2022, and disrupted several government agencies' ability to operate. The attack came against a backdrop of increasing tensions between the two countries, with Russian troop build-ups along the Ukrainian border causing concern that an invasion could be imminent. Chainalysis researchers saw a similar situation unfold in 2017, when tensions between the two nations were also running high. At that time, the Russia-based NotPetya ransomware strain, which contained no viable payment mechanism, targeted several Ukrainian organisations and was also widely judged to be a geopolitically motivated disruption attempt by the Russian military rather than a money-making effort.
Microsoft Security published its own analysis of the recent attack, noting that the ransomware strain in question - dubbed DEV-0586 or more commonly known as WhisperGate - has no way of returning victims' access to their files. Microsoft Security's blog also includes the message the ransomware group displayed to its Ukrainian victims.
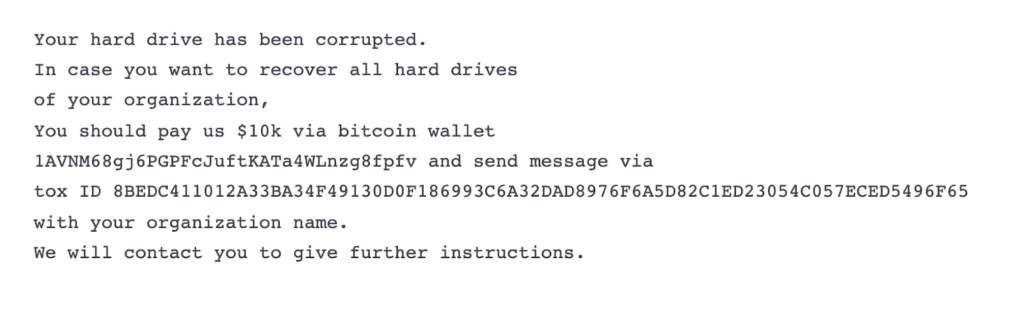
DEV-0586's address doesn't have an extensive transaction history for us to draw from.
Further analysis of the ransomware's technical characteristics indicates even more geopolitical gamesmanship. On 26 January, CERT-UA released a report showing that DEV-0586 contains code repurposed from WhiteBlackCrypt, a ransomware strain active in 2021 that, like DEV-0586, is designed to wipe victims' systems rather than extort them for money.
However, there’s a twist: WhiteBlackCrypt targeted Russian organisations rather than Ukrainian ones.
Cybersecurity analysts believe DEV-0586’s reuse of code previously used by WhiteBlackCrypt, as well as the presence of other similarities linking the two strains, is a gambit by Russian hackers to make DEV-0586 appear to be of Ukrainian rather than Russian origin - in other words, a false flag attack.
The gambit shows how far state actors using ransomware to attack foes will go to conceal their attacks' origins and maintain plausible deniability. Chainalysis researchers have confirmed the team will continue to monitor DEV-0586's address for more activity and provide updates when possible.
Russia-affiliated attackers aren't the only ones using ransomware for geopolitical ends.
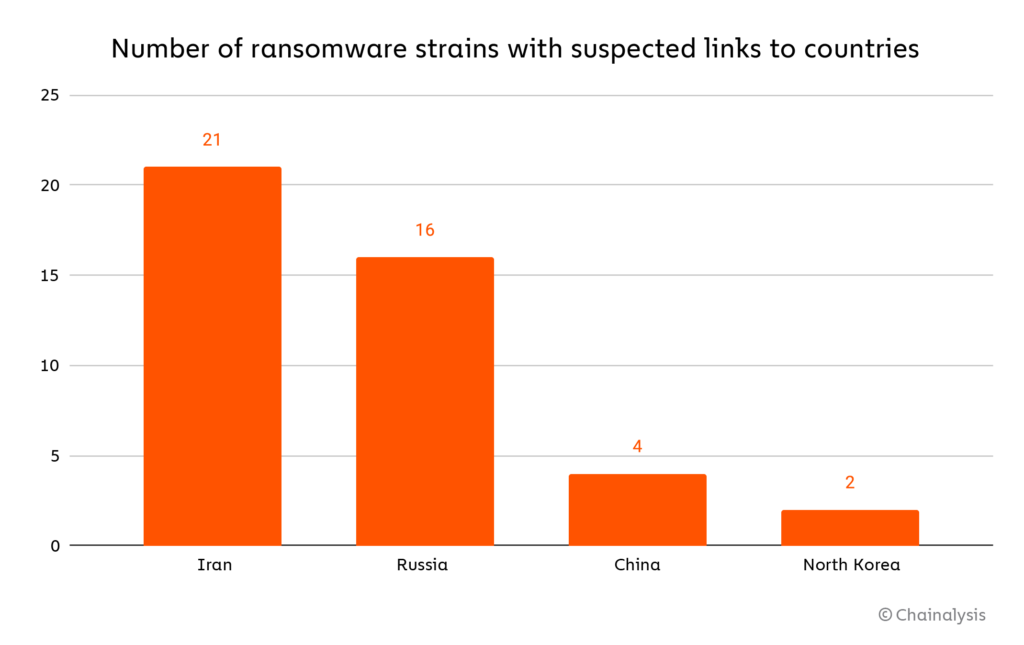
Cybersecurity analysts at Crowdstrike and Microsoft have concluded that many attacks by ransomware strains affiliated with Iran, mostly targeting organisations in the US, the EU, and Israel, are geared more toward causing disruption or serving as a ruse to conceal espionage activity. Generally speaking, Chainalysis researchers have seen significant growth over the last year in the number of ransomware strains attributed to Iranian cyber criminals in the past year - in fact, Iran accounts for more individual identified strains than any other country.
To be clear, Chainalysis researchers have explained many of those Iranian ransomware strains are used for conventional, financially motivated attacks by cyber criminals operating in the country. Iran has a highly educated population but limited occupational opportunities, which likely contributes to the allure of ransomware. However, other strains behave more like tools of espionage, extorting negligible amounts of cryptocurrency from victims. Other analysts have previously identified instances of strains affiliated with China, such as ColdLock, carrying out similar geopolitical attacks on Taiwanese organisations.
Ransomware is a useful cover for strategic denial and deception against enemy states because attacks can be carried out cheaply, and it gives the attacking nation some measure of plausible deniability, as they can always claim the attack was carried out by mere cyber criminals or another nation state.
Even ransomware attacks carried out for non-financial reasons leave a trail on the blockchain. For that reason, it's crucial that agencies focused on national security understand how to trace funds using blockchain analysis, as this is the key to identifying the individuals involved in the attacks themselves, the tools they use, and how they launder any funds obtained from victims.
What’s next for ransomware?
Ransomware isn't just dangerous. It's also one of the most dynamic, constantly changing forms of cryptocurrency-based crime. Between constant rebrands, shifting money laundering strategies, and the influence of geopolitics, it’s hard to know what’s coming next.
According to Chainalysis researchers, one trend to look out for though is Monero ransoms. Analysts have noted that more and more attackers are demanding victims pay in Monero, likely due to the heightened anonymity it offers. While the vast majority of attackers continue to demand bitcoin, law enforcement and cyber security professionals should keep an eye out for ransom notes requesting Monero or assets associated with other protocols with privacy-enhancing features, as this will change the investigative tactics they must employ.
[Related: Department of Health CIO joins xAmplify as head of futures and innovation]
Be the first to hear the latest developments in the cyber industry.