Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Forescout’s Vedere Labs, in partnership with CyberMDX, has discovered a set of seven new vulnerabilities affecting PTC’s Axeda agent, coined as Access:7.

Three of the vulnerabilities were rated critical by CISA, as they could enable hackers to remotely execute malicious code and take full control of devices, access sensitive data or alter configurations in impacted devices.
The Axeda solution is designed to enable device manufacturers to remotely access and manage connected devices.
The affected agent is most popular in healthcare but is also present in other industries, such as financial services and manufacturing.
A detailed list of 150-plus potentially affected devices from 100-plus vendors highlights the significance of the vulnerabilities. The list contains several medical imaging and laboratory devices.
IoT devices use a wide variety of operating systems, hardware and software. Typically, IoT manufacturers do not allow customers to install software, including security agents, on their devices. In the case of Access:7, PTC depends on IoT manufacturers to install the Axeda agent before their IoT devices are sold to customers in what is typically called an original equipment manufacturer (OEM) approach.
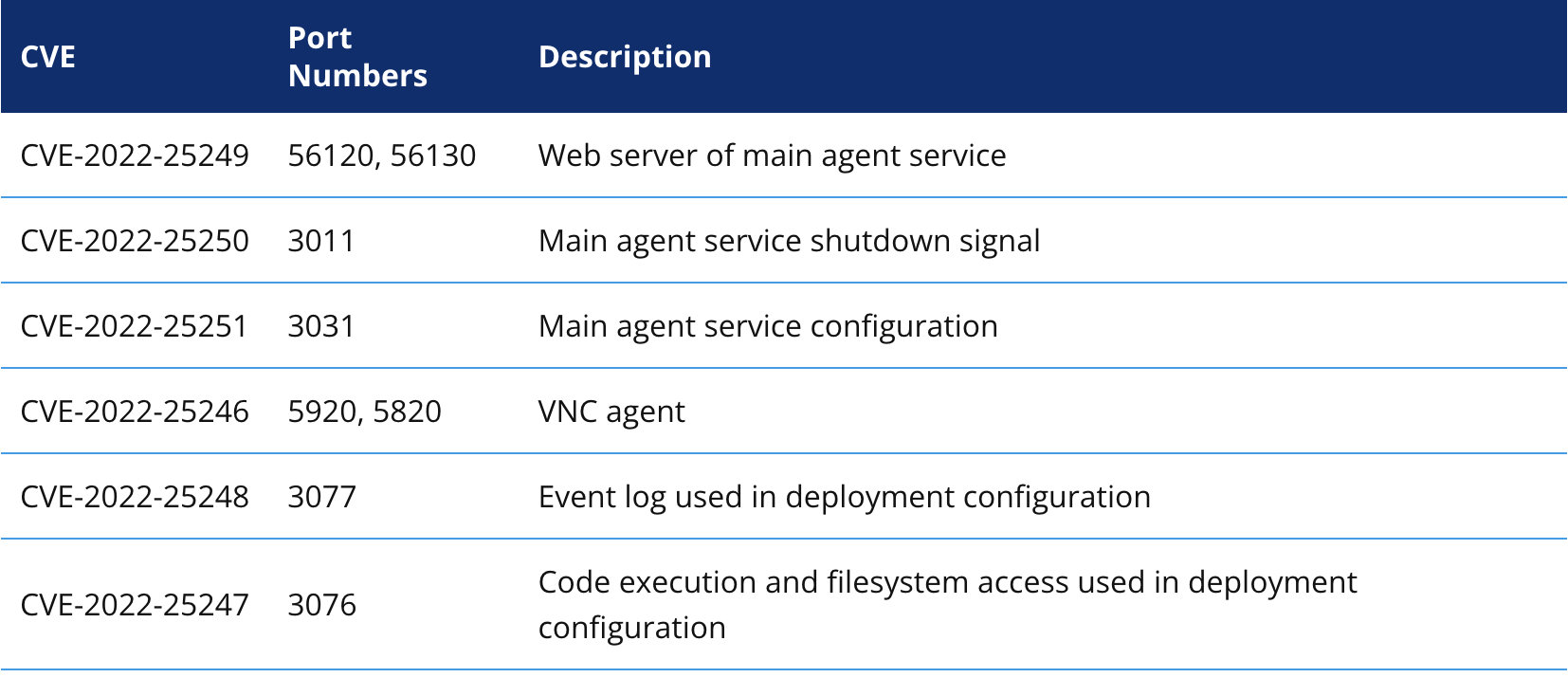
The table below shows the newly discovered vulnerabilities. Rows are coloured according to the CVSS score: yellow for medium or high and red for critical.
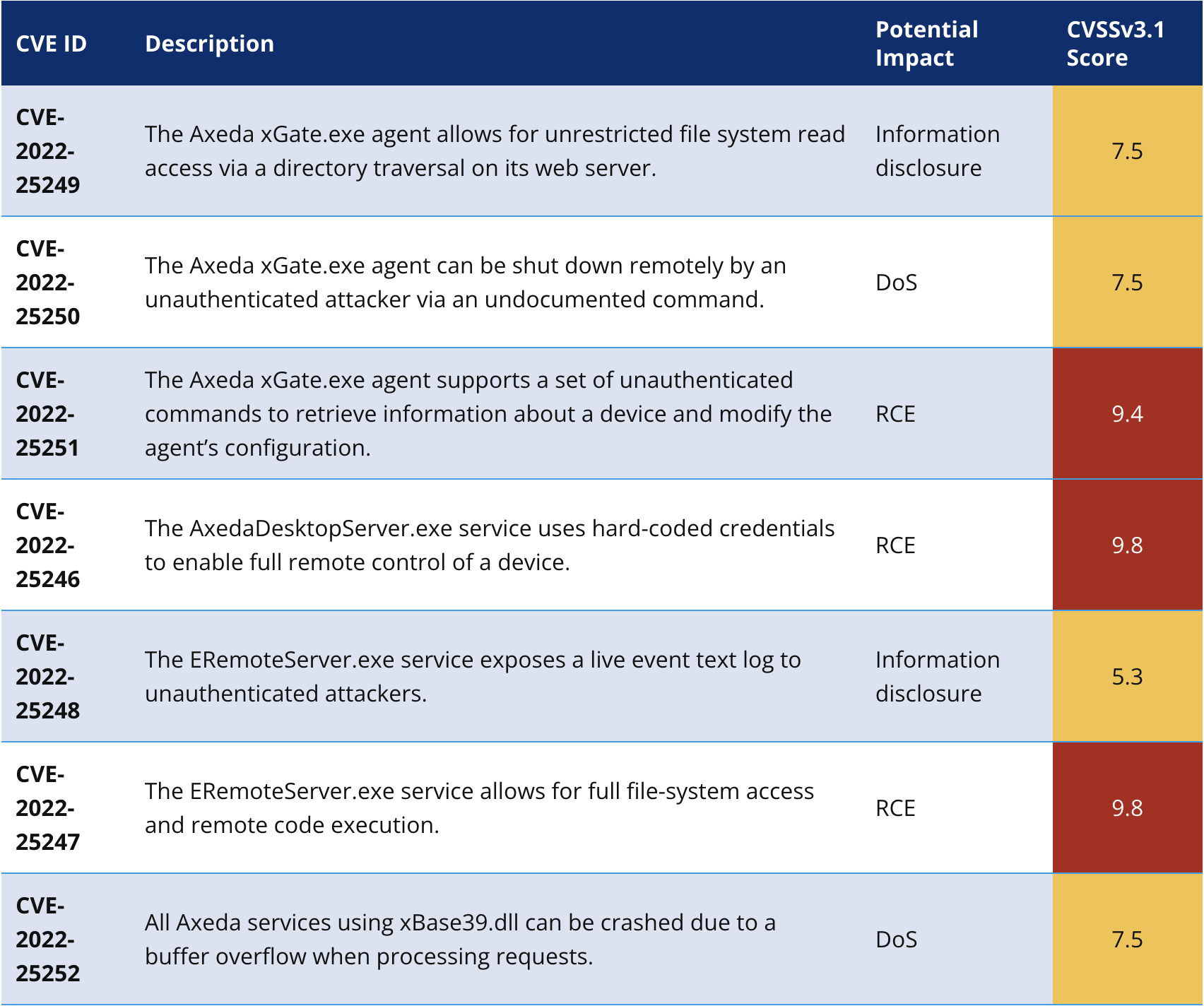
Impact of Access:7 supply chain vulnerabilities on IoT devices
Forescout has populated a list of more than 100 vendors and 150 devices that use the Axeda solution.
Using anonymised customer data in the Vedere Labs Global Cyber Intelligence Dashboard, analysts have seen more than 2,000 unique devices running Axeda on their networks.
By examining these sources, analysts could learn about the potential impact of the vulnerabilities.
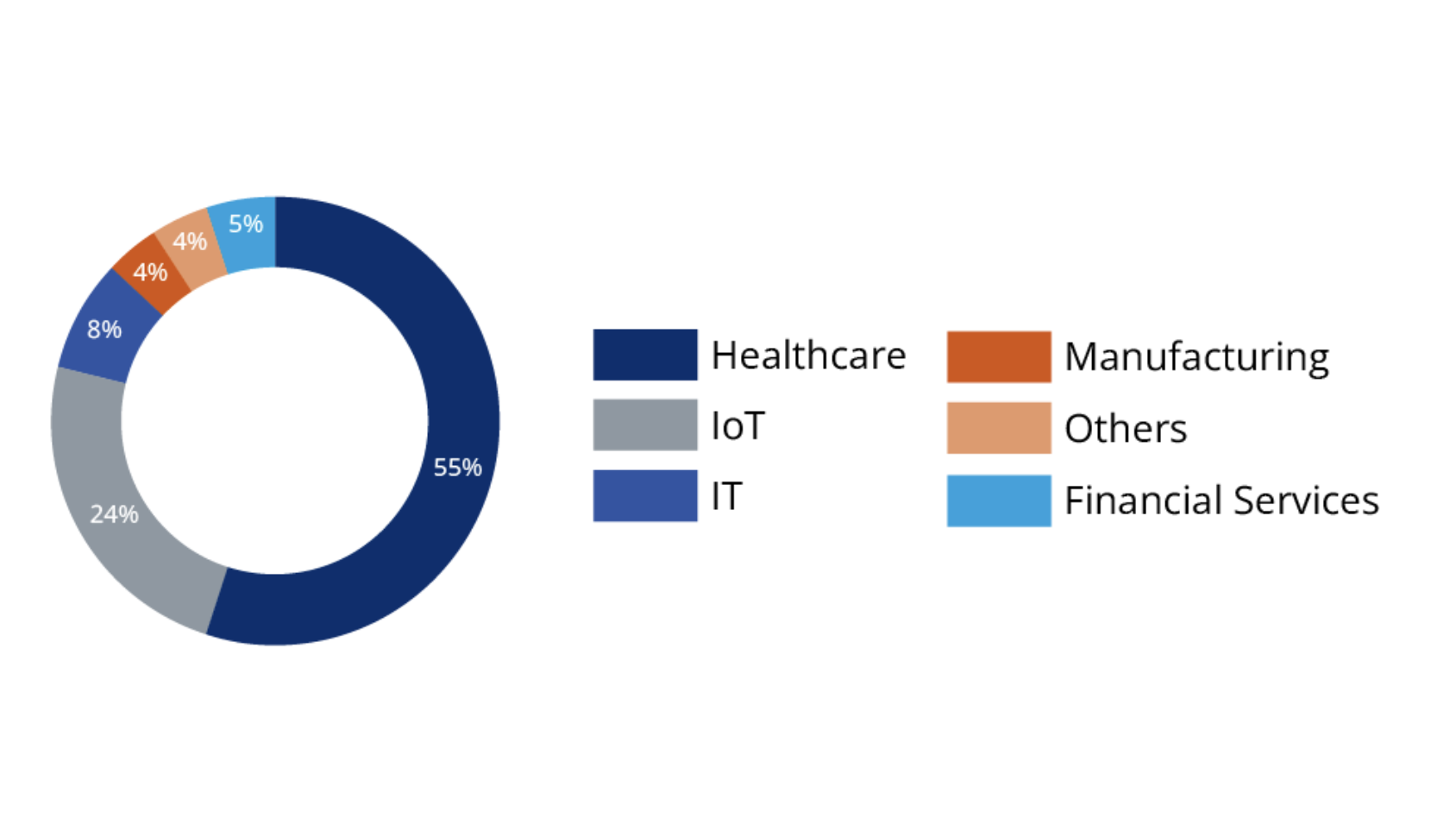
The figure below illustrates the distribution of vendors in our device lake that use Axeda. More than one-half of those (55 per cent) belong to the healthcare industry, followed by almost one-quarter (24 per cent) developing IoT solutions.
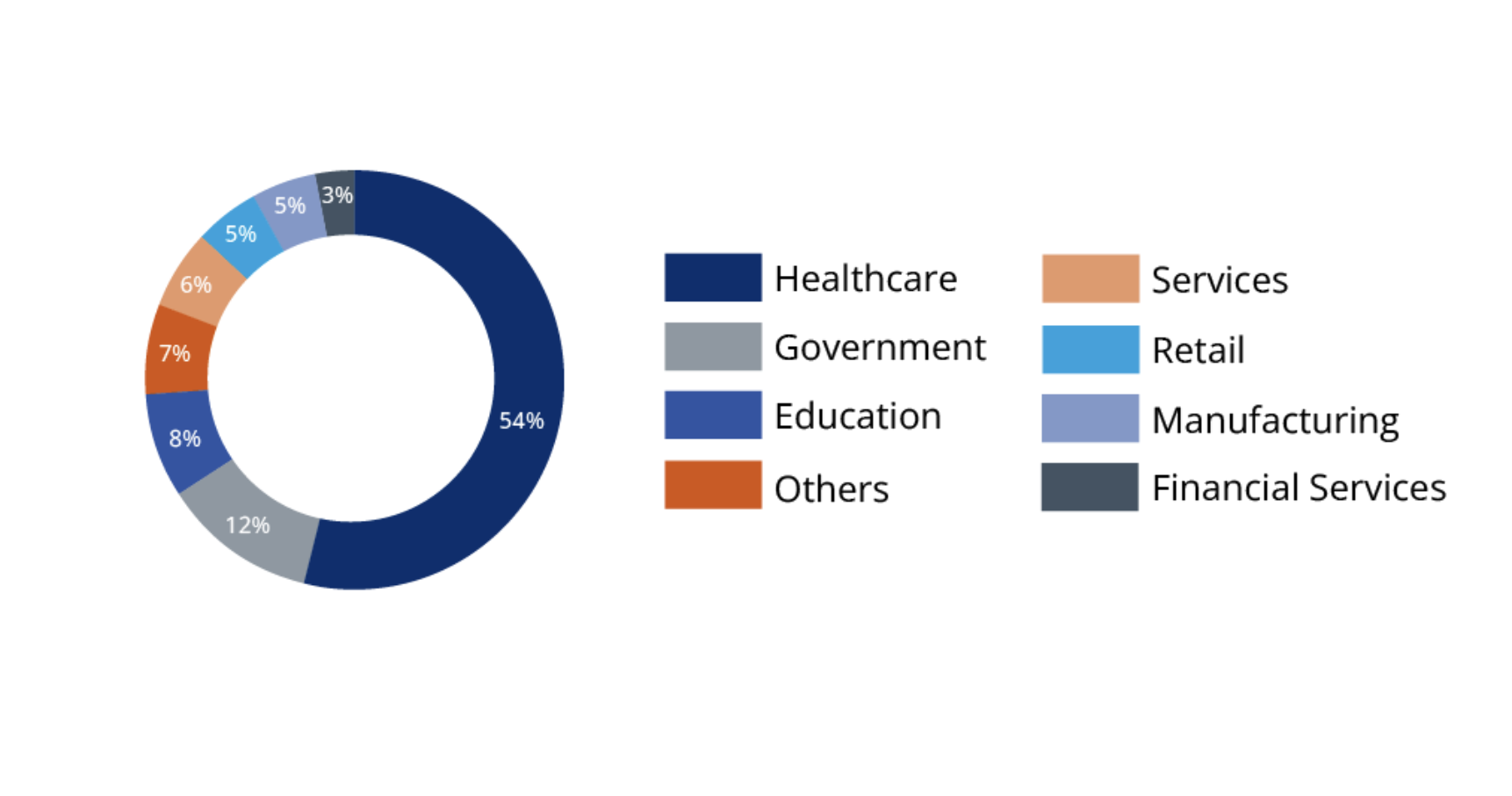
From a device deployment perspective, again analysts see that more than one-half (54 per cent) of the customers with devices running Axeda are in the healthcare sector.
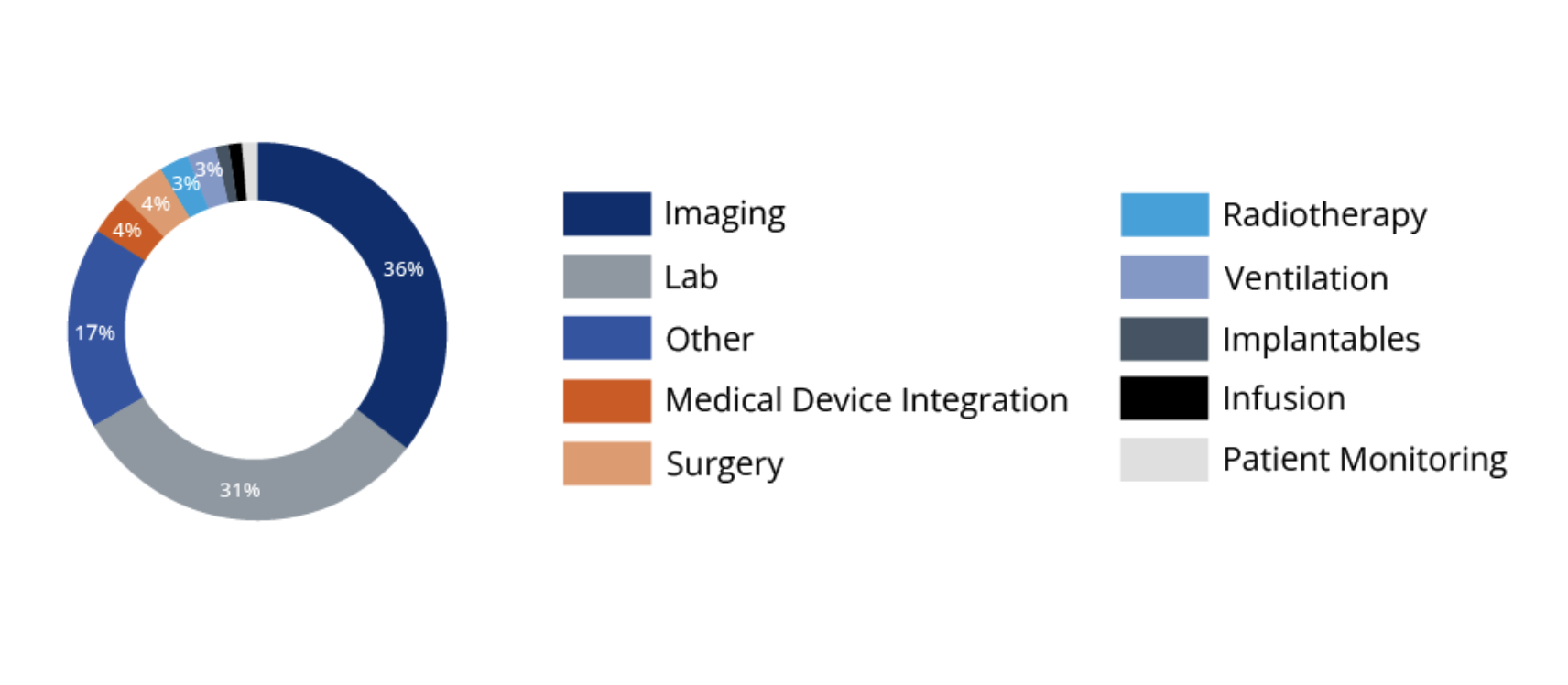
The figure below illustrates the distribution of medical device types running Axeda. The agent was found to be more popular in imaging (36 per cent) and lab (31 per cent) machines than in any other type.
Axeda was developed as a cloud platform for IoT devices, therefore, it is found in a variety of applications beyond healthcare. Vulnerable devices used in other industries include ATMs, vending machines, cash management systems, label printers, barcode scanning systems, SCADA systems, asset monitoring and tracking solutions, IoT gateways and machines such as industrial cutters.
Access:7 mitigation recommendations for network operators
Complete protection against Access:7 requires patching devices running the vulnerable versions of the Axeda components. PTC has released its official patches, and device manufacturers using this software should provide their own updates to customers.
In the technical report, analysts discuss mitigation strategies for device manufacturers. For network operators, analysts recommend the following:
[Related: The 3 trends driving Conti’s Australian ransomware attacks]
Be the first to hear the latest developments in the cyber industry.