Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Secureworks has linked two HUI Loader activity clusters to China-based threat groups based on their new research on HUI Loader, a malicious tool that criminals have been using since 2015.

According to the Secureworks Counter Threat Unit (CTU), the Bronze Riverside threat group is likely responsible for one cluster, which is aimed at stealing intellectual property from Japanese organisations. Another cluster involves deployment of LockFile, AtomSilo, Rook, Night Sky, and Pandora post-intrusion ransomware.
Specifically designed to stay undetected on a compromised machine, loaders are small, malicious packages and their sole purpose is to load and execute additional malicious payloads. The custom HUI Loader is a DLL loader that is deployed through hijacked, legitimate software programs susceptible to DLL search order hijacking. The loader is designed to deploy and decrypt a file containing the main malware payload once executed.
Cyber threat groups including APT10/Bronze Riverside, connected to the Chinese Ministry of State Security (MSS), and Blue Termite have used HUI Loader in previous campaigns. These threat groups have deployed remote access Trojans (RATs) including SodaMaster, PlugX, and QuasarRAT via HUI Loader.
The two activity clusters related to HUI Loader that SecureWorks CTU research team have connected to "Chinese-speaking threat actors" now appear to be adapted to spread ransomware.
The first cluster is tied to Bronze Riverside, suspected to be using the loader to execute the SodaMaster RAT and has been focused on stealing intellectual property from Japanese organisations.
Bronze Starlight has been linked to the second cluster, with activities tailored for IP theft and cyber espionage based on SecureWorks research.
Depending on the information, cyber criminals seeking targets vary. So far, victims include Brazilian pharmaceutical companies, a US media outlet, Japanese manufacturers, and a major Indian organisation's aerospace and defence division.
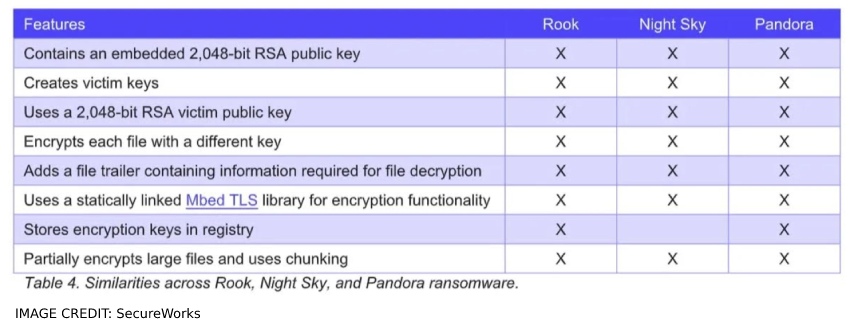
Bronze Starlight has deployed five different kinds of ransomware according to the SecureWorks data post-exploit, which include LockFile, AtomSilo, Rook, Night Sky, and Pandora. The loader is used to deploying Cobalt Strike beacons during campaigns, which create a remote connection, and then a ransomware package is executed.
"The threat actors have developed their versions of the ransomware from two distinct code bases: one for LockFile and AtomSilo, and the other for Rook, Night Sky, and Pandora.
"Based on the order in which these ransomware families appeared starting in mid-2021, the threat actors likely first developed LockFile and AtomSilo and then developed Rook, Night Sky, and Pandora," SecureWorks CTU said.
Avast has a decryptor for LockFile and AtomSilo and it appears other ransomware variants are all based on the Babuk source code.
The loader has also been recently updated as cyber security researchers have found a new version of HUI Loader that uses RC4 ciphers to decrypt the payload. It now has an enhanced obfuscation code aimed at disabling Windows Event Tracing for Windows (ETW), Antimalware Scan Interface (AMSI) checks, and interfere with Windows API calls.
While Chinese government-sponsored groups have not historically used ransomware, SecureWorks researchers believe there is precedent in other countries.
"Conversely, Chinese government-sponsored groups using ransomware as a distraction would likely make the activity resemble financially motivated ransomware deployments.
"However, the combination of victimology and the overlap with infrastructure and tooling associated with government-sponsored threat group activity indicate that Bronze Starlight may deploy ransomware to hide its cyber espionage activity," SecureWorks researchers concluded.
[Related: SolarWinds to release open-source software based on SUNBURST attack learnings]
Be the first to hear the latest developments in the cyber industry.