Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Life comes at you fast when you’re a fledgling ransomware operator, and the newly emerged Ransomed group seems to have learned that the hard way.
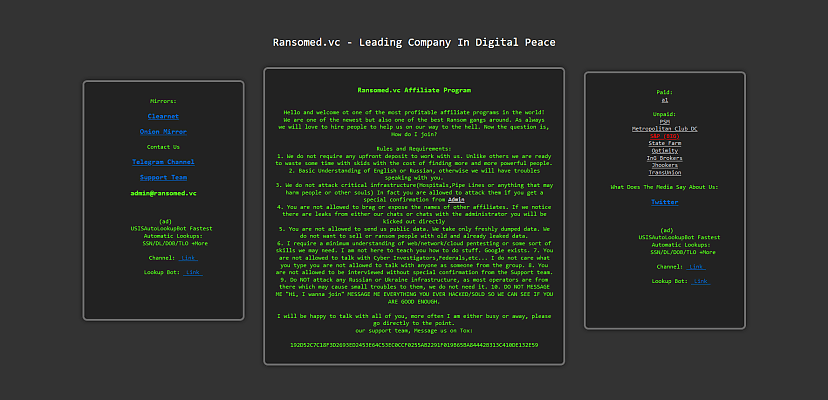
However, it’s also learning very fast, and has begun taking advantage of a wholly new tactic to extort its victims.
The Ransomed group first built itself up as a forum – RansomForums – on 15 August 2023, according to researchers at Flashpoint. They registered their domain and began advertising themselves on Telegram, alongside starting their own Telegram channel.
However, within days, the site was hit with a DDoS attack – probably from another ransomware group. Ransomed then shifted to a more traditional ransomware blog-style format, where they could threaten to publish the data of their victims if a ransom was not paid.
But that’s where Ransomed parts from tradition.
Ransomed is now calling itself the “Leading Company in Digital Peace Tax”, an attempt to legitimise itself as something more akin to a public service than a criminal enterprise. This itself is not entirely new – many ransomware operators consider themselves akin to very expensive pen-testers – but its methods of extortion are novel.
Rather than simply threatening to publish data, Ransomed is using data protection laws such as GDPR to get its victims to pay up. The ransom amounts are typically far less than what a GDPR fine might add up to, making paying an even more desirable outcome.
“I heard you do not wanna pay me?” the group asks one of its victims on its Telegram channel. “Well then lets (sic) start with leaking a few customers to the public. I wonder what the GDPR agency will think about our relationship?”
According to Ransomed’s own site, the group does little of its own hacking, instead operating as an affiliate program recruiting other hackers to do the work.
“It is unclear right now whether Ransomed uses a specific ransom variant, or extorts victims only through leaked information,” Flashpoint said in a blog post. “Its channel initially claimed the group was looking for affiliates and has since closed recruiting efforts and declared that enough individuals have joined them – there is no further evidence of how the group conducts its attacks.”
So far, the group lists just nine victims, with one seeming to have paid, one whose details have been “removed by request”, though may be listed again if payment is not forthcoming, and the rest are either unpaid or in the process of paying up.
The group is upfront about where it’s based, asking possible affiliates to refrain from attacking targets in Ukraine or Russia, as “most operators are from there”. Other stipulations include not attacking critical infrastructure without permission, and that all supplied data must be original, and not from prior leaks.
As Flashpoint points out, it is very early days for the group, and verifying that they have the data they claim can be difficult.
“The ascent of Ransomed onto the cyber threat stage is a reminder of the uncertainties that exist in the cyber threat intelligence landscape,” Flashpoint concludes, “where early impressions can often shift dramatically with the acquisition of more data.”
The group clearly has big plans for the future, however - it is already recruiting heavily.
"We are seeking five people for a TEAM, not basic affiliate program but a TEAM," the group posted recently on Telegram. "Skills in Web/Network/Pentesting is a need."
Watch this space, more or less.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.