Share this article on:
Powered by MOMENTUMMEDIA
Breaking news and updates daily.
Ever wanted to use police powers to track people down on social media?
Well, if you answered yes to that, firstly – don’t. It’s illegal in a range of ways, in a whole mess of jurisdictions.
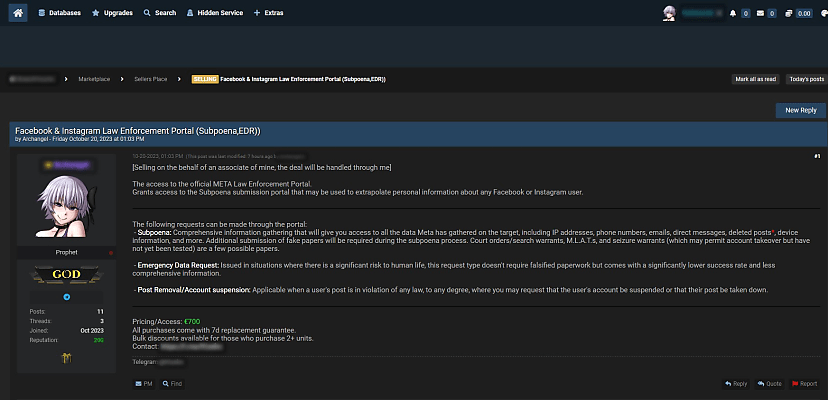
But, hypothetically speaking, if you did want to do it, an enterprising member of a popular clear web hacking forum is selling access to Facebook uber-company Meta’s Law Enforcement Portal for a mere €700.
According to the post, the deal comes with a seven-day replacement guarantee, and the seller is even offering “bulk discounts” for purchasing more than one set of credentials.
Access to the portal allows law enforcement officers to subpoena information on a given user, including their IP address and private messages, though the seller does note that anyone attempting this will need some corroborating material.
“Comprehensive information gathering that will give you access to all the data Meta has gathered on the target, including IP addresses, phone numbers, emails, direct messages, deleted posts, device information, and more,” the post said.
“Additional submission of fake papers will be required during the subpoena process. Court orders/search warrants, MLATs, and seizure warrants (which may permit account takeover but have not yet been tested) are a few possible papers.”
An MLAT is a mutual legal assistance treaty, which law enforcement agencies often use in cross-jurisdictional matters.
Access to the portal also allows for the removal of posts or suspension of accounts and for emergency data requests.
“Issued in situations where there is a significant risk to human life, this request type doesn’t require falsified paperwork but comes with a significantly lower success rate and less comprehensive information,” the poster said, suggesting some familiarity with the level of access they are selling.
At least one forum user has already been directed to contact the seller privately to discuss a possible sale.
In a LinkedIn post, security researcher Alon Gal pondered how the threat actor gained access to the portal.
“I can speculate that either Meta was social-engineered by someone to gain this kind of access, or the threat actor had credentials for a legitimate law enforcement account,” Gal speculated over the weekend.
The initial post was made on 20 October.
We have reached out to Meta for comment.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.